The TOP 6 Fallacies of Cyber-Threat Hunting

Focus on what will make it work
#6
It is more TACTICAL than STRATEGIC. The current small community addressing why “Threat Hunting?” should not be relying on high-level theoretical punditry such as…
“Know your IT environment.” -OR-
“Think like a Hunter.”
These strategic points of view only move the “needle” slightly in favor of companies and agencies fighting the daily cyber-assaults on their systems and data. There is a need to begin delving into the details. It is no longer a matter of what needs to be done, and now it is time for the cybersecurity community to define how to do it.
#5
Threat Hunting is NOT purely focused on endpoint detection. The gravest concern is the focus on the threats already “in the wire.” It is too late if the threat has already penetrated your firewalls. The real objective is the integration of homogeneous (internal) audit-log type data, and heterogeneous (external) threat intelligence to improve the odds of organizations to push back cyber-threats.
#4
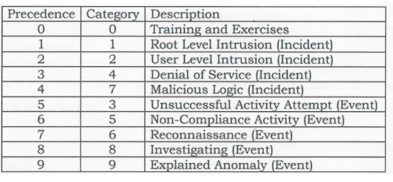
It is not “normal” versus “abnormal.” How do you define “normal?” This understating of anomaly detection is overly simplistic. For example, what may appear as abnormal to some may in fact be typical activity over the Internet for the seasoned cyber-forensic specialist. This kind of poor consideration fails to provide enough granularity to determine the kinds and levels of threat to the IT infrastructure. A preferred approach is the Department of Defense’s (DOD) “Precedence Categorization” (see chart below). It provides a good means to prioritize potential attacks from a less-than-defined event to an actual incident.
#3
It is not about “magical” intuition on the part of threat hunting activity. The Threat Hunters and supporting operational and intelligence personnel are professionals and are not clairvoyants. This kind of language makes it appear as a less-than repeatable and scientific process. It is not just an educated guess, but experiential expertise that is created by the teamwork that occurs within a defined threat hunting group.
ADOO Loop
#2
The OODA loop is REACTIVE, NOT PROACTIVE. Air Force Colonel John Boyd was a maverick for his time and a hero for his insight for a parochial Air Force of the time. The small community of Threat Hunting expertise is still fighting with a 20th Century model not designed for an evolving cyber-threat. Boyd’s model worked well for pilots in dogfights but has little applicability in cyber-threat hunting. It should be reversed and be proactive on Day 1. It should become the ADOO model for cyber-threat hunting purposes.
- ACT—Create an environment that already puts the bad-guy on the defense. Use honeypots and security devices that can both detect and PREVENT the attack in the first place.
- DECIDE—Determine what is working well and what is not. Variability is your greatest asset against an ever-evolving threat.
- ORIENT—Identify where efforts have been and will be most successful. Identify common attack vectors and have solutions that can either mitigate or stop the success of the attacks within the IT environment. The longer the threat is “in the wire”, the more damage they can cause.
- OBSERVE—Conduct lesson learned sessions after every attack—document what was learned. Learn from mistakes, and adjust personnel, resources, and approaches for the next attack.
The worst advice is that Threat Hunting
should be Aggressive.
#1
It is NOT “aggressive.” That is the worst public advice. Taking an aggressive stance against cyber-attacks opens the company or agency to the potential full weight of a highly committed and resourced Advanced Persistent Threat (APT) such as China, Russia, or Iran. Threat Hunting should not go beyond its IT security boundaries. This should include cloud environments, backups, and alternate sites. The companies and agencies should never engage in a hack-back. It is never recommended. Cyber-Threat Hunting is an active assertive activity that must quickly identify and stop the threat. Unless you are a sovereign nation-state with the resourcing and technical capabilities to respond to attacks against your networks, being aggressive is never a good idea.

Dr. Russo is currently the Senior Data Scientist with Cybersenetinel AI in Washington, DC. He is a former Senior Information Security Engineer within the Department of Defense’s (DOD) F-35 Joint Strike Fighter program. He has an extensive background in cybersecurity and is an expert in the Risk Management Framework (RMF) and DOD Instruction 8510, which implement RMF throughout the DOD and the federal government. He holds a Certified Information Systems Security Professional (CISSP) certification and a CISSP in information security architecture (ISSAP). He has a 2017 Chief Information Security Officer (CISO) certification from the National Defense University, Washington, DC. Dr. Russo retired from the US Army Reserves in 2012 as a Senior Intelligence Officer.









