COMMENTARY: DOD’s “NEW” CMMC is unnecessary duplication

The ONLY change needed is the introduction of third-party assessors to resolve the one real flaw of RMF
“The current estimate of companies and businesses requiring CMMC certification is over 300,000.”
In 2019, the Department of Defense (DoD) announced the development of the Cybersecurity Maturity Model Certification (CMMC). The CMMC is a framework not unlike NIST 800-171.
The CMMC is intended to serve as a means ensuring the most appropriate levels of cybersecurity controls are active. This will require contractors to protect controlled unclassified information (CUI) that resides on the Department’s industry partners’ unclassified networks.
It is an unnecessary duplication of the National Institute of Standards and Technology (NIST) 800-171 with ONE significant difference. CMMC is nothing more than an evolution of NIST 800-171 with elements “borrowed” from NIST 800-53 and ISO 27001—the change is only the addition of third-party auditing.
Even though the DOD describes NIST SP 800-171 as different from CMMC and it will implement “multiple levels of cybersecurity,” the addition of third-party auditing, will be the only real change….
In addition to assessing the maturity of a company’s implementation of cybersecurity controls, the CMMC will also assess the company’s “maturity/institutionalization of cybersecurity practices and processes.” The security controls and methodologies will be the same—the DOD still has not recognized the apparent duplication.
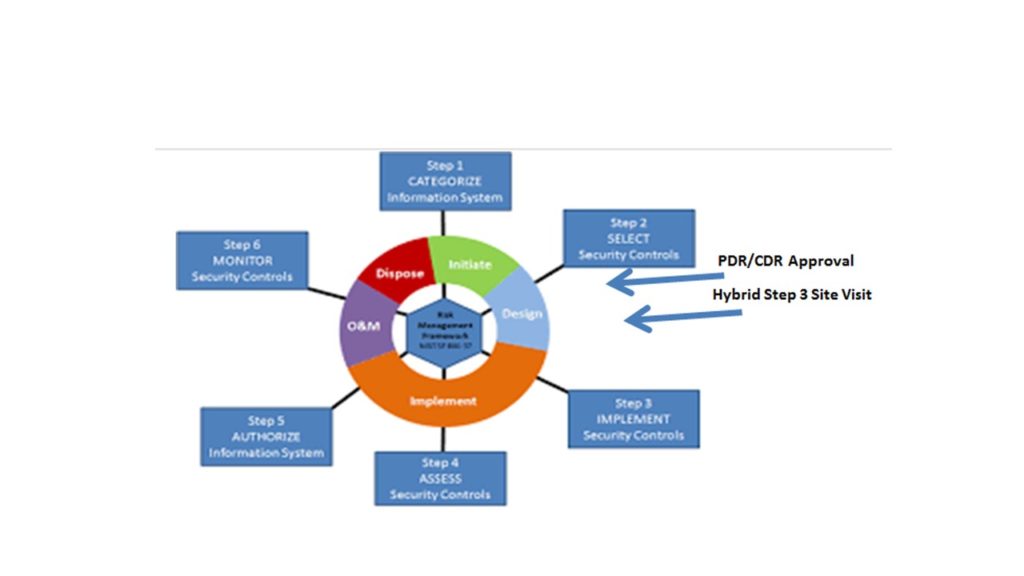
The DOD will require third-party assessment of a company’s Information Technology (IT) system and data protection measures using the same NIST controls as based the foundational federal NIST framework, NIST 800-53 revision 4 (with revision 5 pending). The CMMC is initially focused at DOD’s Defense Industrial Base (DIB) partners and is specific to Controlled Unclassified Information (CUI)protection measures, and NOT national security designated information or data.
Formerly, NIST 800-171 allowed for self-assessment by contractors; however, the CMMC does not permit this current weakness of NIST 800-171. It recognizes that the technical capabilities of the defense contracting community have historically been inadequate and incomplete from the small through large defense contract communities. When it comes to an understanding of the Risk Management Framework (RMF), CMMC is a result of past poor cybersecurity contracting management and oversight by the federal government to include the DOD.
The federal government has been plagued for years NOT by the lack of cybersecurity frameworks, but an unwillingness to enforce contractual requirements from vendors at the detriment of the safety and security of the nation.
Contractors will now be required to be certified by a third-party auditor. The Department of Defense is currently pursuing information, from non-profit organizations, related to establishment of an Accreditation Body for the CMMC program. There has been no guidance to-date of what certification a CMMC auditable company must have—who is auditing the auditors?
Furthermore, the Defense Contract Management Agency (DCMA) and the Defense Counterintelligence and Security Agency (DCSA) will have a purview overview the CMMC. If history bears true, neither of these agencies have the needed funding or expertise to provide the incredible need for services by tens of thousands of contractors–and subcontractor!! They have neither the capabilities nor experience to execute the CMMC framework.
Cybersecurity defense within the DOD is expected to struggle as it attempts to understand and deploy capabilities for which it has limited organic capabilities.
[Ref: “The Cost of Malicious Cyber Activity to the U.S. Economy, CEA” in February 2018].
The Council of Economic Advisers, an agency within the Executive Office of the President, estimates that malicious cyber activity cost the U.S. economy between $57 billion and $109 Billion in 2016
CMMC is expected to include portions of various cybersecurity standards, such as NIST 800-171, ISO 270001, and ISO 27032; however, at its core, NIST 800-53 is the universally accepted standard for DOD systems. NIST 800-53 will provide the basis of any standards of best security practices and a measure of the “maturity of a company’s institutionalization of cybersecurity practices and processes.”
Furthermore, the cost of certification will be allowable and as a reimbursable cost as part of typical contract negotiations under the Defense Federal Acquisition Regulation Supplement (DFARS). While the current guidance states that the costs “will not be prohibitive,” the DOD has yet to identify the tasks and activities required to conduct auditing that meets the CMMC “standard.”
For additional and updated information, it is best to continually check the Office of the Under Secretary of Defense for Acquisition and Sustainment website at https://www.acq.osd.mil/cmmc/index.html. The DOD is planning to release Version 1.0 of CMMC by January 2020; however, expect it to be delayed is as typical to these extensive—but critical—efforts by the DOD. Contractors are expected to include CMMC costs in future proposals by June 2020; however, expect that to be delayed more likely into 2021-2022 time frames.


Dr. Russo is currently the Senior Data Scientist with Cybersenetinel AI in Washington, DC. He is a former Senior Information Security Engineer within the Department of Defense’s (DOD) F-35 Joint Strike Fighter program. He has an extensive background in cybersecurity and is an expert in the Risk Management Framework (RMF) and DOD Instruction 8510, which implement RMF throughout the DOD and the federal government. He holds a Certified Information Systems Security Professional (CISSP) certification and a CISSP in information security architecture (ISSAP). He has a 2017 Chief Information Security Officer (CISO) certification from the National Defense University, Washington, DC. Dr. Russo retired from the US Army Reserves in 2012 as a Senior Intelligence Officer.









