Powerflows are designed to capture in a graphical format, a simplistic or better representation of the many challenges faced in cybersecurity. It offers the novice through professional pictorial representations to help them better understand and approach current problems in cyberspace.
If you have your own graphics, please send to admin@cybersentinel.tech. We will give you credit and an opportunity to share your innovative ideas with your fellow cybersecurity specialists.
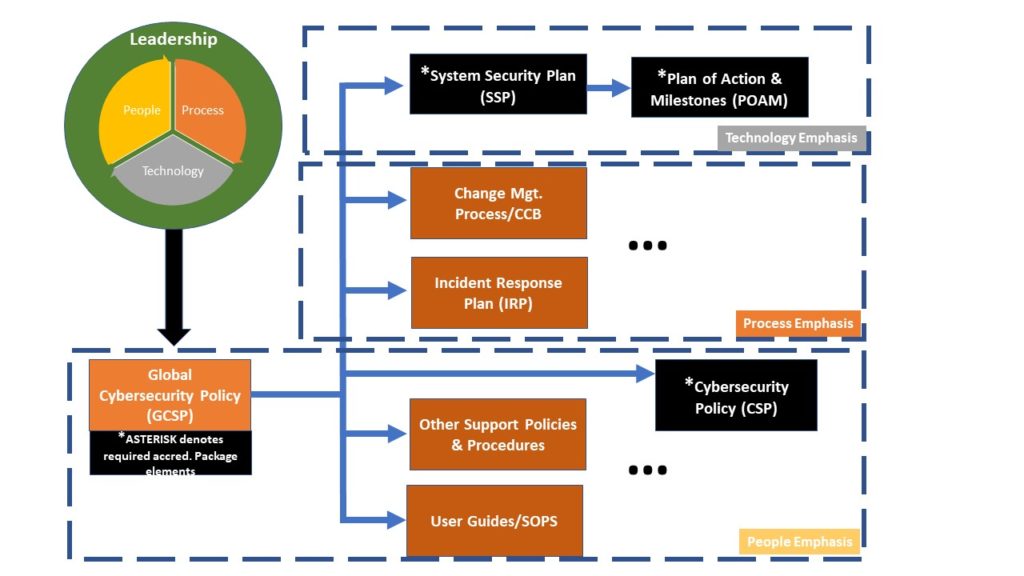
Security Authorization Development Package Model (SADP-M)
[NIST 800-171 and the CMMC]
This model introduces the Global Cybersecurity Policy (G-CSP). It forms the starting-point for required accreditation documentation under NIST 800-171–with applicability to CMMC. This is a defined process to help created auditable packages for accreditation. The assigned IT professional or ISSO will subsequently populate and provide answers to the auditor in the G-CSP. After this work is completed, the ISSO will begin to “strip out” the other documents to include the SSP, CSP, POAM, etc.
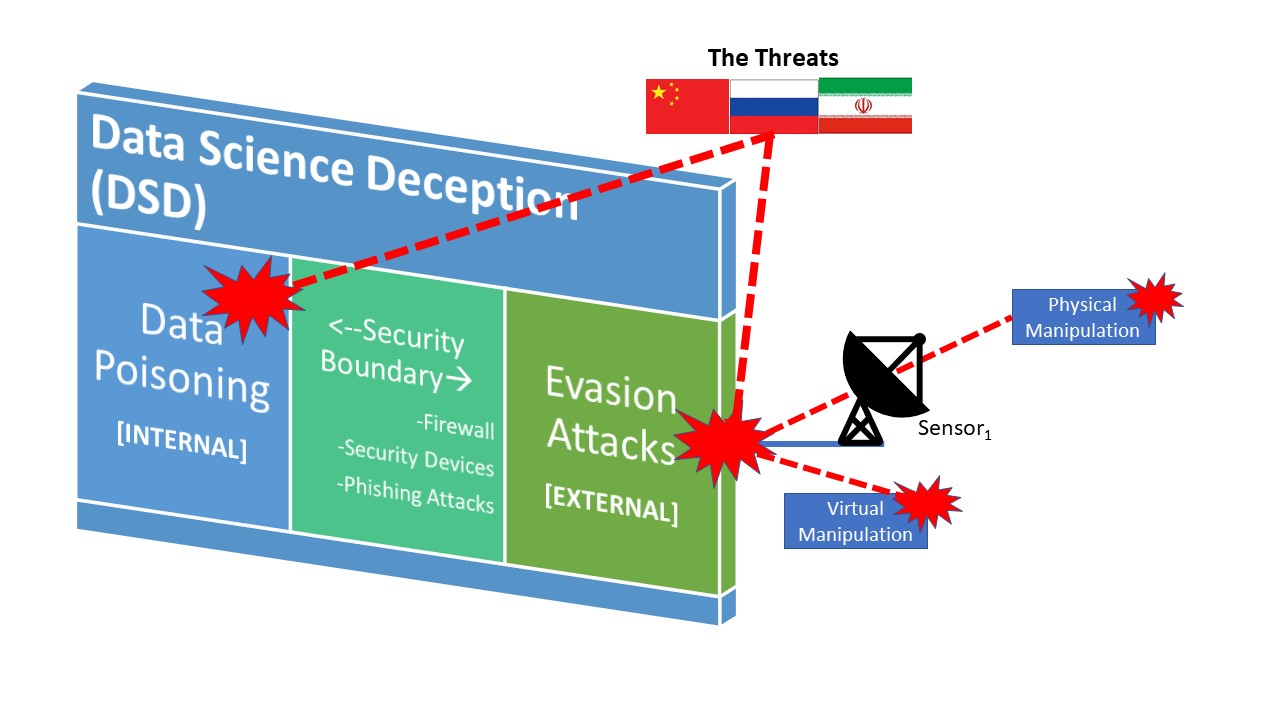
Data Science Deception (DSD)
In 2019, I asked a professor at the National Defense University (NDU) about Dr. Hurley’s article, Enabling Successful Artificial Intelligence Implementation in the Department of Defense (Hurley, 2018), what Dr Hurley meant about data manipulation by foreign threats specific to data collection. Were these threats destined to manipulate the data before it was collected or after it had already been retrieved by the researcher in the confines of their networked data repository? He stated: “both.”
(See 2020 Blog Post)
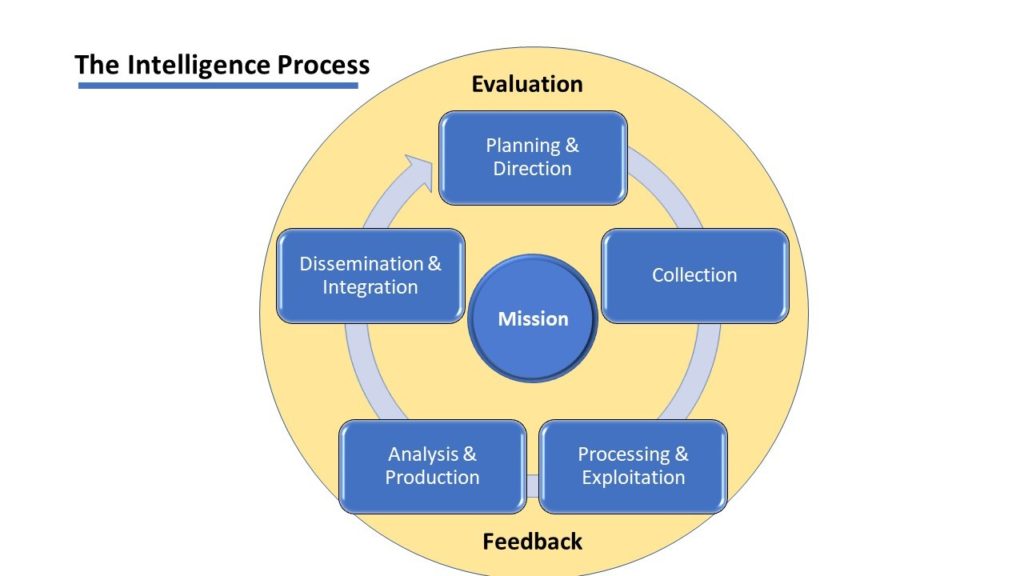
More Threat Hunting
The Master Threat Hunting Database plays a critical part in intelligence collection, analysis, and processing. It starts with the CTI team (or individual).


Cyber-Deception
What do we do when our failed efforts have been focused for too long on Prevention alone?
Prevention has been less-than successful for the defense of our modern-day networks. Daily we hear about another cyber-intrusion, and pure automated solutions such as deploying smart firewalls, anti-virus software, etc., has not stopped the “bad guys.” An emerging and related capability that could enhance Threat Hunting is the advent of Cybersecurity Deception (CD) as an adjunct to any good Threat Hunting effort. A move to a holistic CD planning and execution approach offers a serious solution to countering the daily barrage of cyber-threat attackers. CD is that next opportunity for the Cybersecurity community to create a next-generation model for future success.





From a mathematical expression view, CCM can be described by the following:
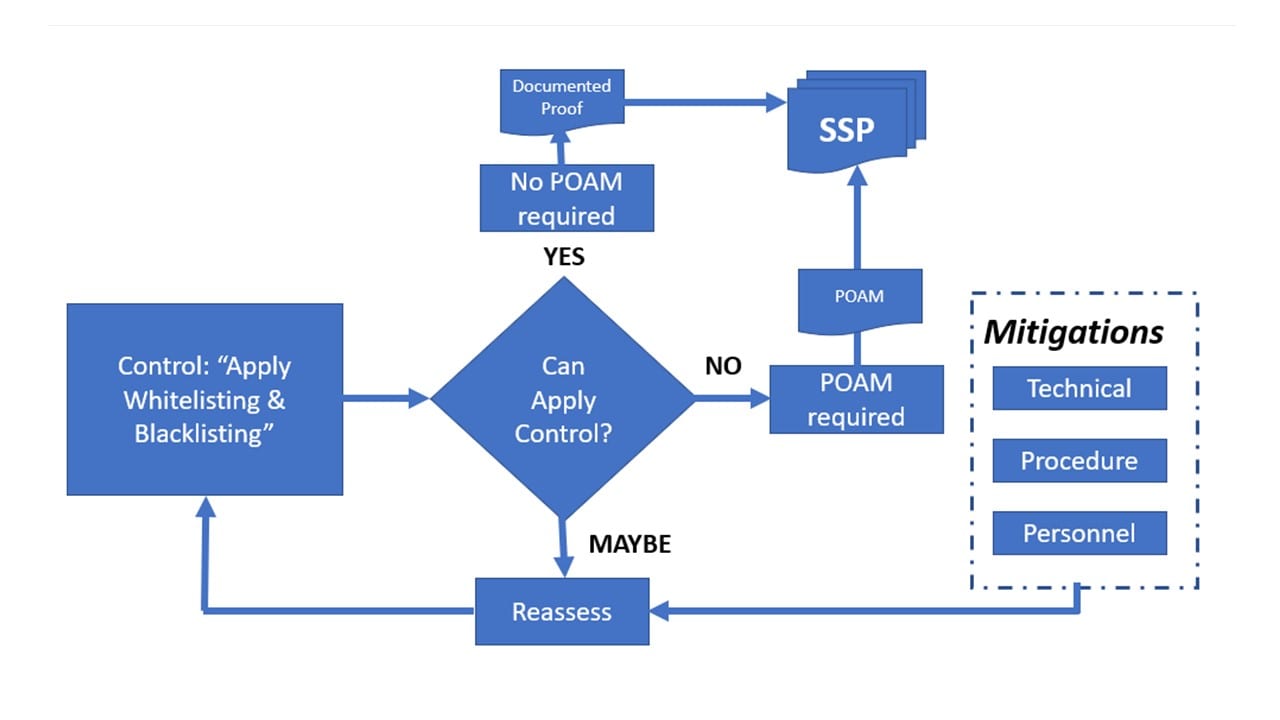
Basic Plan of Action & Milestones (POAM) Decision-Tree
The PPT Model
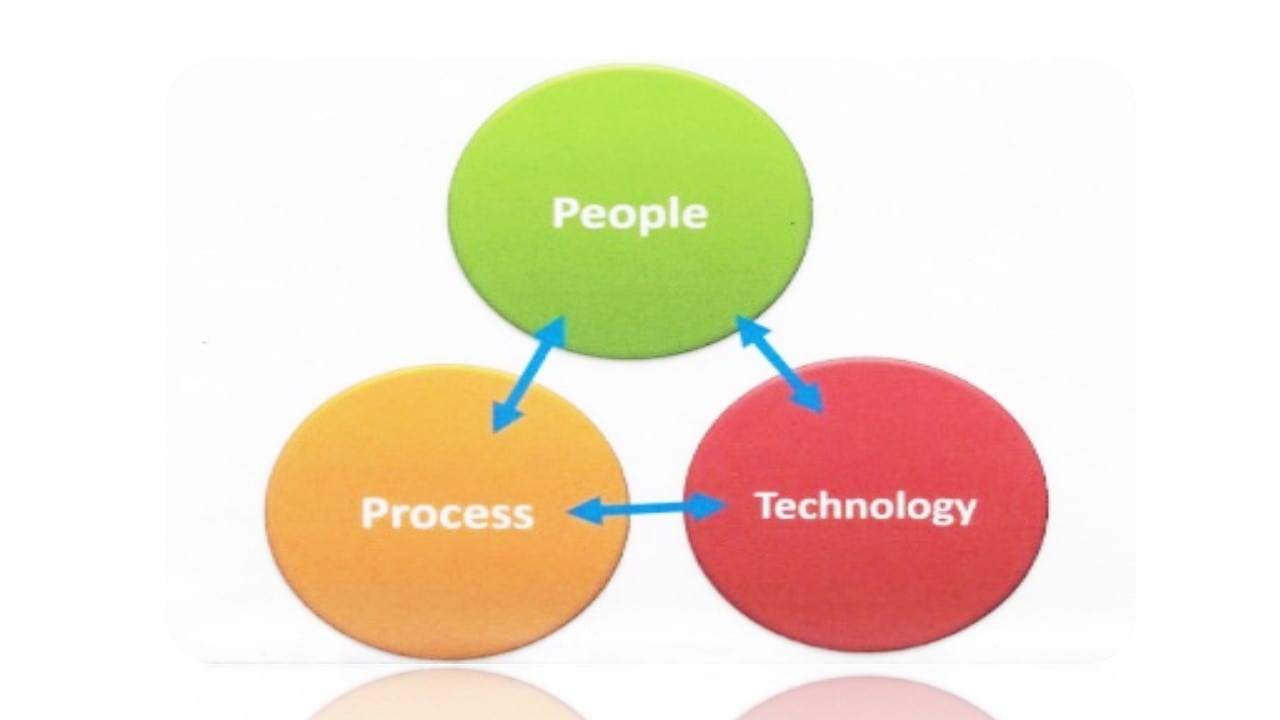
One of the simpler, but more powerful models of how to best address a vulnerability or control finding. It recognizes that a POAM solution does not just need to be about a technical solution alone. The People and Process components are just as important in fixing a finding, and long-term, they are probably the better solutions set.
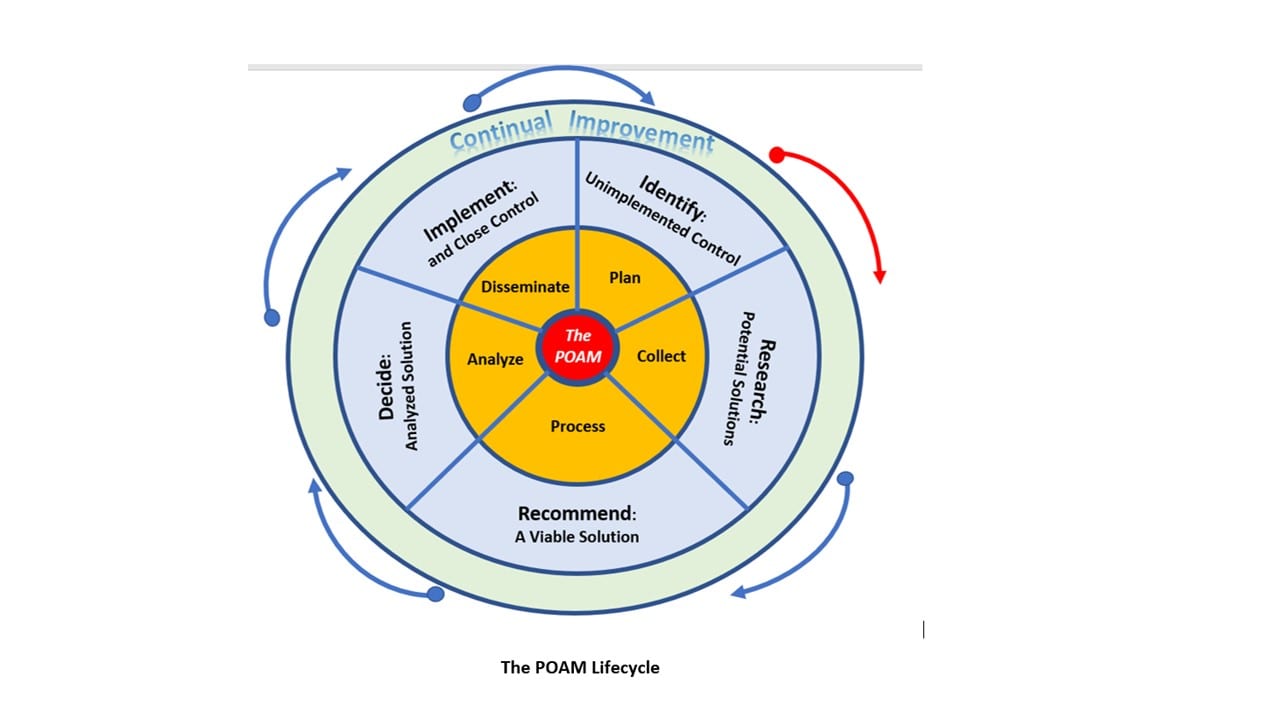
The POAM Lifecycle
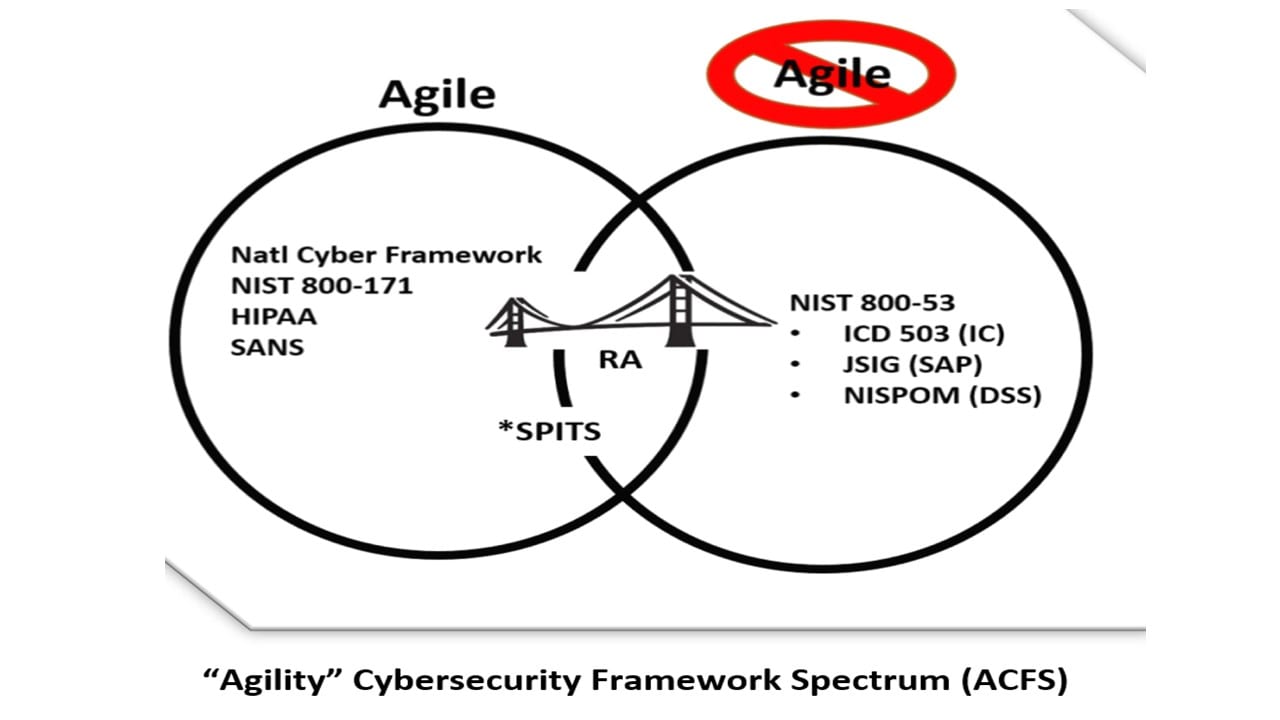
Agile & Non-Agile NIST Frameworks
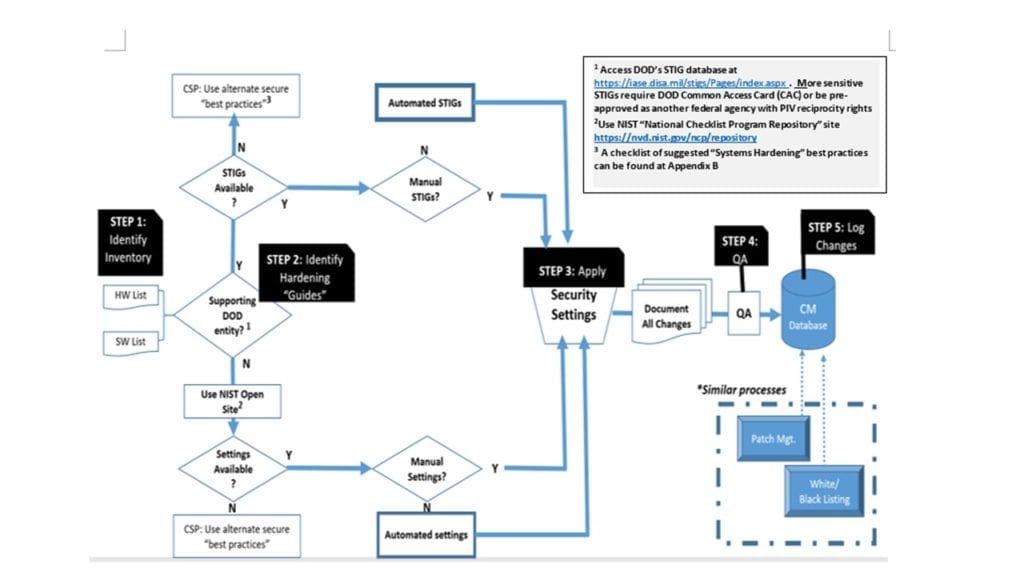
System Hardening Decision-Tree