New Social Media Site to Follow Us On (Twitter)
We are now on Twitter. A second way to follow our blog posts and updates.... @sentinel_cyber ... Cyber Sentinel Some...
 Data Scientists v. Statisticians: Delineating Roles and Effective Deployment
Data Scientists v. Statisticians: Delineating Roles and Effective Deployment
 Cyber Threat Hunting (CTH) in an Age of Escalating Cyber Threats
Cyber Threat Hunting (CTH) in an Age of Escalating Cyber Threats
 Should You Hire a Virtual CISO?
Should You Hire a Virtual CISO?
 TOP 5: The Main Implications of ML to Help Deter Cyber-threats
TOP 5: The Main Implications of ML to Help Deter Cyber-threats
 CYBER DECEPTION: Impact to Cybersecurity and the Application of Machine Learning Tools
CYBER DECEPTION: Impact to Cybersecurity and the Application of Machine Learning Tools
 TOP 10: Challenges of NIST 800-171 for Companies to Meet DOD Cybersecurity Contracting Requirements
How the DOD Can be Successful against the Major Cyber Threat Actors?
TOP 10: Challenges of NIST 800-171 for Companies to Meet DOD Cybersecurity Contracting Requirements
How the DOD Can be Successful against the Major Cyber Threat Actors?
 The Importance of Continually Learning into Adulthood
The Importance of Continually Learning into Adulthood
 Clustering Algorithms Can Play a Pivotal Role in Identifying Cyber-threat Anomalies in Data
Clustering Algorithms Can Play a Pivotal Role in Identifying Cyber-threat Anomalies in Data
 SPOT: Security Technical Implementation Guides (STIGs): Why are They Neglected by System Developers?
SPOT: Security Technical Implementation Guides (STIGs): Why are They Neglected by System Developers?
We are now on Twitter. A second way to follow our blog posts and updates.... @sentinel_cyber ... Cyber Sentinel Some...
A Recent Cybersecurity Question Raised from within the F-35 Joint Strike Fighter Program Imagine your bank is audited every...
Expectations Beyond DOD In late 2018, the expectation is that the United States (US) federal government will expand the National...
Is a DDOS Considered an "Armed Attack"? In this post, we look at what may occur diplomatically, politically, and militarily...
111F Supp 2d 294(U.S. Dist. Ct., So Dist. NY, 2000) Historical and legal considerations that play a role in policy...
Emerging Technology Bandwidth demands are growing exponentially. “Leading service providers report bandwidth doubling on their backbones every six to nine...
A Look at How China's Huawei Technologies Company is under the persistent observation of the United States Introduction In February...
An essay on the role of how HUMAN beings play a vital role in the future of data analytics ...
How NIST 800-171 May Be The Better Solution To-date The CCPA provides California residents the right: To know what personal...
This is how ED supports cybersecurity As recently as 2017, the Department of Education (ED) only afforded $600 per year...
An Opportunity to Show Your Expertise We are looking for 3 guest-bloggers to help us refine this entry of the...
NIST Frameworks that Fit In the age of lean and agile development, can “Agile Cybersecurity” fit into these paradigms? Is...
Defining Continuous Monitoring Cybersecurity is not about shortcuts. There are no easy solutions to years of leaders demurring their responsibility...
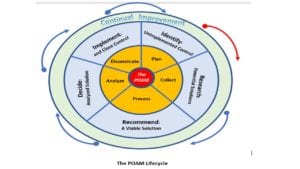
What is the best way to think about the POAM Lifecycle? In Brief Using the US Intelligence Community’s Intelligence Cycle...
Our Inaugural Release! "The Cyber Sentinel" is dedicated to "the good, the bad and the ugly of cybersecurity." WEEK 2:...
An Introduction to a young cyber-software developer looking to help us be more secure Frank is a budding young programmer...
A Disjointed and Bureaucratic Mess The principle of Risk Management (RM) has been a failure for the federal government’s implementation...