Cybersecurity Deception: A Matter of an Active-Defense

What do we do when our failed efforts have been focused on prevention?
DEFINITION:
CYBER-DECEPTION: Deliberate actions to obfuscate the threat from collecting complete and actionable intelligence about a defended Information Technology (IT) security boundary.
The classic solution for deception has been the honeypot. Norton defines honeypots “…as a computer or computer system intended to mimic likely targets of cyberattacks. It can be used to detect attacks or deflect them from a legitimate target. It can also be used to gain information about how cybercriminals operate [1].” It is not only about cybercriminals, but nation-state actors, individuals, and “hive minds” such as Anonymous; the honeypot, as just one common example, poses both an active and passive form of cybersecurity defense.
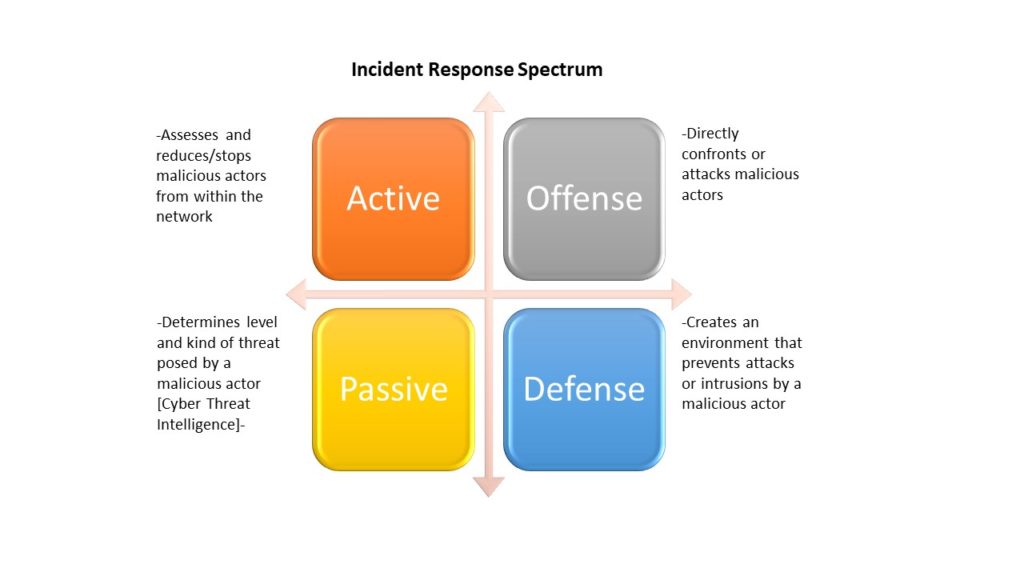
Cybersecurity Deception (CD) employs three main elements for success; the honeypot is only one way to use all elements of strategic deception as a tactical means. The passive portion is its existence and appearance as an actual targeted network; it is the purest form of deception. However, if it is not convincing or reputable to the would-be attacker, it is easily dismissed and bypassed. The threat may recognize this as a deception and further attempt to penetrate the actual network; the work to establish a misleading setting is only as good as its appearance as a genuine working IT environment. The more active-passive approach results from both the simple IT deception in coordination with a more engaged collection of information and intelligence about an attacker and his Tactics, Techniques, and Procedures (TTP).

What more is needed?
It is important to implement a Strategic Cybersecurity Deception Plan (SCDP) within the deception lifecycle. It is composed of the following elements:
- GOALS/OBJECTIVES: What can you accomplish within your available resources? Can you develop multiple virtualized database servers with dummy data or can you just employ a single server behind the firewall that creates a diversion from your main data repositories? Your goals and objectives should be constrained by two major sub-components:
- Resources: People, dollars, and skills, AND
- Risk tolerance: What damage may result to your company or agency based upon a data breach? Can your reputation survive a data loss or are other mitigation strategies possible?
- TACTICAL DECEPTION: How can you create a plausible IT environment that either causes the threat to be diverted from your infrastructure as a target or causes them to move elsewhere? Can you appear as a more complex environment that creates multiple false targets for an attacker?

- CREATE THE ENVIRONMENT: Apply the resources and deception plan into a physical environment. Identify what additional resources may be needed such as specialized equipment or third-party security providers.
- EXECUTE: At this point in the lifecycle, begin to conduct both passive and active operations to accomplish your major goals/objectives. Additionally, this approach requires ongoing review to include:
- CONTINUOUS MONITORING: Collect necessary threat data, such as Indicators of Compromise (IOC), such as file names, Internet Protocol (IP) addresses, hash “fingerprint” values, etc.
- CONTINUOUS IMPROVEMENT: Continue to appear as a legitimate network by adding and modifying the deception network over time.
- CONTINUOUS MONITORING: Collect necessary threat data, such as Indicators of Compromise (IOC), such as file names, Internet Protocol (IP) addresses, hash “fingerprint” values, etc.
Prevention has been less-than successful for the defense of our modern-day networks. A move to a holistic Cybersecurity Deception (CD) planning and execution approach offers a serious solution to countering the daily barrage of cyber-threat attackers. CD is the next opportunity for the Cybersecurity community to create a likely model for future success.
Reference
[1] Norton. (2019). What is a honeypot? [Blog post]. Retrieved from
https://us.norton.com/internetsecurity-iot-what-is-a-honeypot.html

Dr. Russo is currently the Senior Data Scientist with Cybersenetinel AI in Washington, DC. He is a former Senior Information Security Engineer within the Department of Defense’s (DOD) F-35 Joint Strike Fighter program. He has an extensive background in cybersecurity and is an expert in the Risk Management Framework (RMF) and DOD Instruction 8510, which implement RMF throughout the DOD and the federal government. He holds a Certified Information Systems Security Professional (CISSP) certification and a CISSP in information security architecture (ISSAP). He has a 2017 Chief Information Security Officer (CISO) certification from the National Defense University, Washington, DC. Dr. Russo retired from the US Army Reserves in 2012 as a Senior Intelligence Officer.









