PATHWAY: Supply Chain Risk Management (SCRM) 1.0 Framework
A Cybersecurity “Strawman” Offering
Supply chain risks include the insertion of counterfeits, unauthorized production, tampering, theft, insertion of malicious software and hardware (e.g., GPS tracking devices, computer chips, etc.). It also includes poor manufacturing and development practices in the supply chain that introduces or creates risks to the IT system or environment. These risks are realized when threats to the supply chain further create or exploit existing vulnerabilities.
Furthermore, SCRM vulnerabilities if not caught early may take weeks, years, or decades to be launched based upon the objectives and desires of the adversary. It may be difficult to determine whether an event was the direct result of an intentional or unintentional supply chain vulnerability. This may result in an adverse effect on an agencies or businesses operations and missions. This may include degradations to service levels that could lead to customer discontent, theft of intellectual property, or reductions of mission functionality. The common understanding of supply chain risk, and especially SCRM, are focused on the acquisition of computer and IT-based hardware and software components to support modern day IT environments. These may include base network infrastructures and associated systems that are attached to these “backbone” networks to conduct business or operations.
A Roadmap
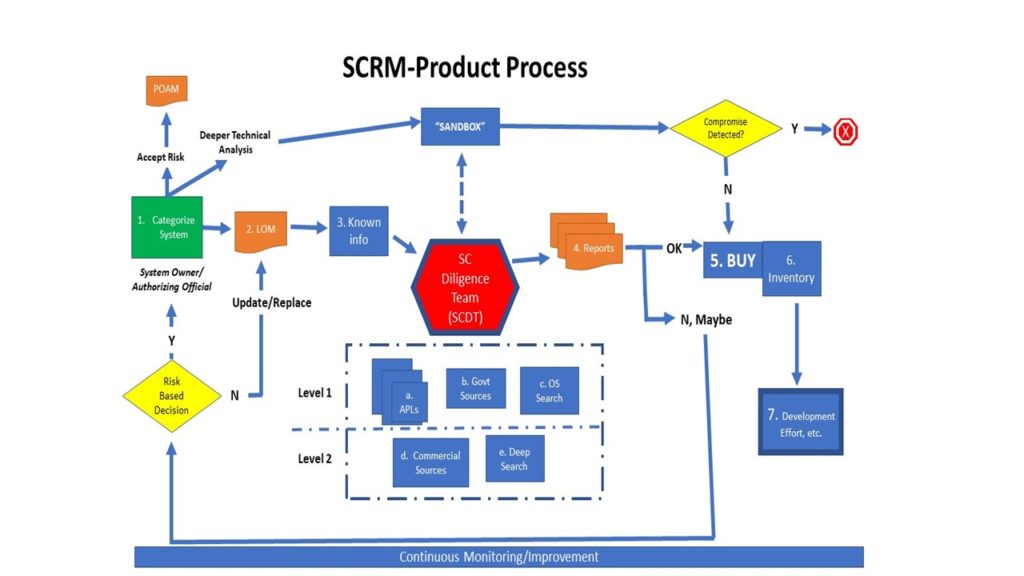
The general concept for establishing an effective and repeatable SCRM 1.0 process is outlined in the Flowchart below, SCRM 1.0 (Product) Process. The focus is on hardware and software products that constitute most of the current-day SCRM challenge. This will include an initial engineering design that should include requirements documents, technical drawings, and target hardware and software lists that will become a major part of the List of Materials (LOM) [2–maps to the flowchart]. Additionally, these listings become a critical component of any cybersecurity package and are typically part of the System Security Plan (SSP).
The process begins with the classic National Institute of Standards and Technology (NIST) 800-53 approach. The “system owner,” working with assigned cybersecurity professionals determine the system categorization [1]. The categorization will either be high, moderate, or low. The overall categorization will drive the level of effort and the number of security controls required to protect the system.
System Categorization
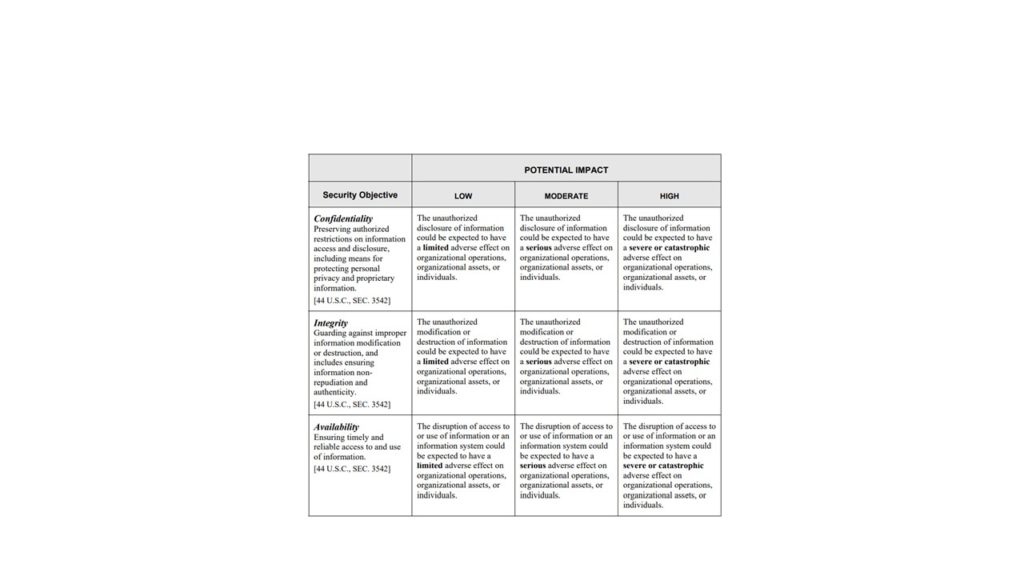
System Categorization should follow the principles as outlined in NIST Federal Information Processing Standards (FIPS) Publication 199, Standards for Security Categorization of Federal Information and Information Systems, February 2004. The following table provides the general descriptions of the “Security Triad” of Confidentiality, Integrity, and Availability (CIA), and the associated definitions based upon their impact levels/dangers to the IT system or environment.
The system owner will use the HIGH WATERMARK principle in the final selection of the system categorization. The selection will be based upon the highest potential impact from among the three security objectives. The following are simplified examples of how to apply the high watermark principle.
The system is rated by the highest rating found in the chart below:
| Confidentiality | Integrity | Availability | High Watermark Selection |
| H | M | L |
H |
| M | L | L |
M |
| L | L | L |
L |
| H | H | M |
H |
| L | M | H |
H |
A List of Materials (LOM) [2] are generated for the system owner with the assigned project manager and logistics staff supporting the effort. This becomes the basis of the hardware and software list as discussed above and are required for a key artifact of the security accreditation effort, the System Security Plan (SSP).
Flowchart for SCRM 1.0

After the LOM is established and reviewed by the logistics support staff, they will identify key details about the materials [3]. This should include public and known information common to the purchase of the equipment, hardware, software, etc. This will be critical to a Supply Chain Diligence Team (SCDT) review. Logistics will provide details such as:
- Make
- Model
- Manufacturer
- Country of origin
- Memory
- Processing speed
- Chip type
- Third-Party Resellers
- Warranties
- Service Level Agreements (SLA)
- Frequency operation ranges
- Radio Frequency (RF) interference
Supply Chain Diligence Team
The SCDT will begin the most vital part of the SCRM 1.0 phase. They will begin by conducting a much deeper analysis of the purchases. This team will conduct a review of by using various public and private databases to determine whether there are any restrictions or concerns about their use based upon the original sensitivity and categorization of the overall system by the system owner and all support staff members. This should include Approved Product Lists (APL), general government sources, and open source searches using basic search engines such as Google®, Bing®, etc.
A Level 2 search is required for a HIGH categorization. This may include access to government restricted classified databases, proprietary commercial sources, or deep/dark web searches requiring greater capabilities and resources by the agency or business. These inputs are used to assess the risk to the overall system. The SCDT will generate reports [4] to other analysts and leaders requiring the information to make future risk-based decisions that may be required later.
Assuming the SCDT does not find any concerns or restrictions about their purchase, the system owner will authorize their buy [5], conduct inventories [6] as they are delivered, and directed to the development effort [7] within a System Development Life Cycle (SDLC) effort typical of current development methodologies and practices.
If the components are found to be either unacceptable or questionable, they will enter the risk-based decision process. If the system owner disapproves of the component, the LOM will be updated, and a suitable replacement identified; it will reenter the process [2] and follow the same workflow.
If the system owner is willing to accept some level of risk, there will be two possible decisions. The system owner will either accept the risk in full, and cybersecurity professionals or other designated IT staff members will create/populate the systems Plan of Action and Milestones (POAM) artifact. The POAM listing will be reviewed regularly to determine whether the components risk should continue to be accepted or replaced because of the dangers and risk to the project.
| Category |
Suggested POAM Review Cycle |
| At Least: | |
| High | Every quarter |
| Moderate | Every 6 months |
| Low | Annually |
Deep Analysis
If desired, a deeper technical analysis may occur by certified/qualified individuals usually from the SCDT. Third-party assessors with the requisite skills and tools may also be used to determine the risk posed by the product purchased. This deeper analysis should occur in a designated “sandbox” environment not connected to any active or operational networks. Assessment may use software and hardware designed to identify any malicious code, improper transmissions to outside Internet Protocol (IP) addresses or ports, etc. The designated experts from the SCDT should play an integral part of any reports to determine risk posed.
If a compromise is detected, it is highly recommended that the product be removed and designated as a threat. The business or agency should notify the appropriate agency in accordance with its Incident Response Plan (IRP); it is vital that the results of the technical analysis is shared as widely as possible to notify and update databases supporting the SCRM process. If no compromise is detected, and the system owner approves, the component may be bought [5] to meet the system needs of the organization.
Continuous Monitoring v. Continual Improvement
The final and long-term effort should include continuous monitoring. Continuous Monitoring (ConMon) should be an active part of the overall cybersecurity protection effort. ConMon should reassess over time the state of IT purchases to identify and determine any changes during the life of the system. It is especially critical for those products that have received a POAM, and their threat to the system needs be minimized based upon its sensitivity to the organization. There are several sub-components that also comprise the ConMon effort to include, but not limited to:
- Vendor changes
- Software Patching
- Anti-virus/Anti-malware updates
- Operating System changes
- Changes in multi-factor access (e.g., biometric upgrades, etc.)
Continuous improvement should also be the goal of leadership to improve the SCRM process. This may include adding additional logistics reviews, enhanced skills training for SCDT personnel, or updated tools to better protect the system. Continuous improvement should include recurring lessons learned meetings and repositories to enhance the organizations knowledge management efforts. Reports, spreadsheets, databases, and repositories should be integral tools to ensure improvement of the supply chain protection efforts.
So What do you think?

Dr. Russo is currently the Senior Data Scientist with Cybersenetinel AI in Washington, DC. He is a former Senior Information Security Engineer within the Department of Defense’s (DOD) F-35 Joint Strike Fighter program. He has an extensive background in cybersecurity and is an expert in the Risk Management Framework (RMF) and DOD Instruction 8510, which implement RMF throughout the DOD and the federal government. He holds a Certified Information Systems Security Professional (CISSP) certification and a CISSP in information security architecture (ISSAP). He has a 2017 Chief Information Security Officer (CISO) certification from the National Defense University, Washington, DC. Dr. Russo retired from the US Army Reserves in 2012 as a Senior Intelligence Officer.