The 6-Step Incident Response Plan(IRP) Roadmap

A Quick-Start Guide
Use the Cyber Incident Life Cycle to guide the company’s operational incident-handling artifact/procedure. This should be an annex to the System Security Plan (SSP).
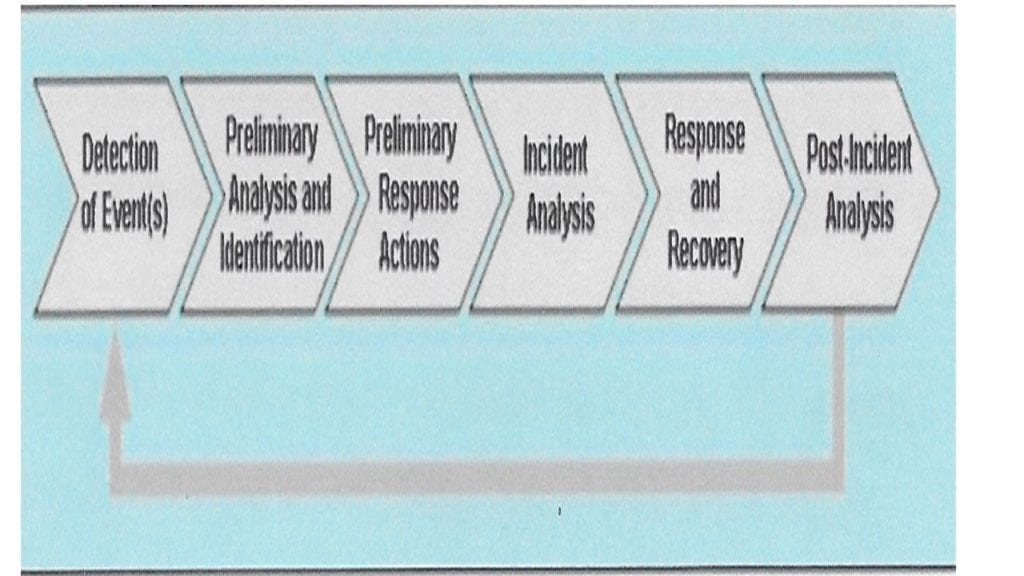
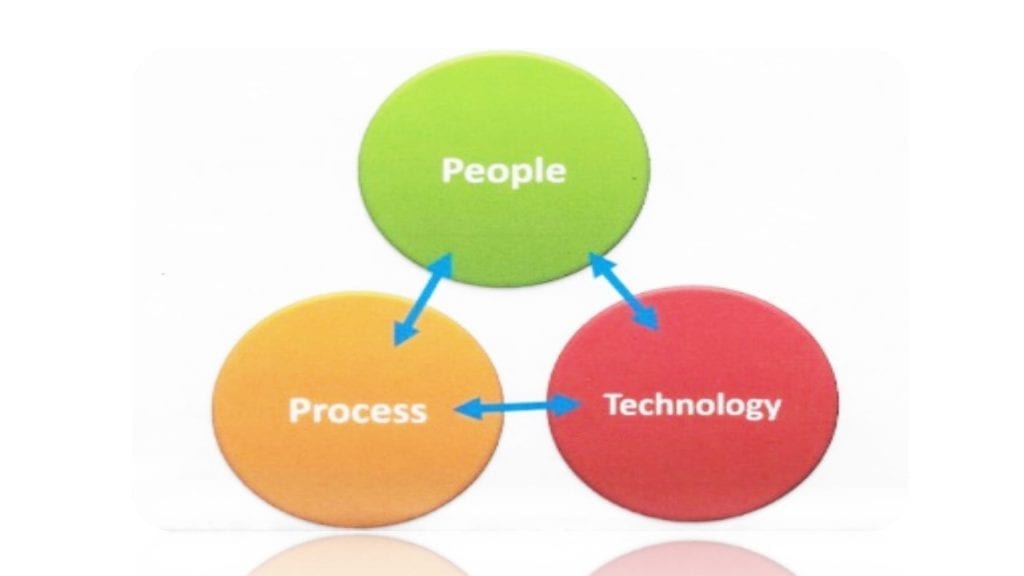
Additionally, the PPT “Model” can be used to guide and formulate the IR Pan annex. A suggested approach is described below, and includes the kinds of questions that should be answered to demonstrate best how best to formulate a good IRP.
1. Preparation
- People: Who will perform the action or activity? Training needed? Skill sets?
- Process: Training policies for cybersecurity and IT professionals to support the IRP.
- Technology: What technology already exists to support IR? What technologies are needed?
2. Detection
- People: Are IT staff able to use audit tools properly to detect intrusions?
- Process: What are ‘best practice’ approaches to detect intrusions? Monitor firewall logs? Monitor user activity?
- Technology: Is the technology’s data library current? Are automatic updates enabled?
3. Analysis
- People: Are IT staff capable to do the analysis required? Can they determine false positive activity?
- Process: What is the process leadership wants to get effective and actionable data from IT staff? What are the demands for immediate and final reporting timelines?
- Technology: Are the right tools on-site? Can open source/web solutions useful? Can DOD or DHS provide helpful data feeds to remain current of threats?
4. Containment
- People: Can IT staff stop the ongoing attack? Do they require additional coding scripting skills to build/update firewall policies?
- Process: Is the containment process effective? Is allowing the attack to continue to identify the threat entity/location a good idea (to support law enforcement)?
- Technology: Can software tools quarantine and stop a malware attack? Is shutting down all external connections a good immediate solution (at the firewall)?
5. Recovery
- People: Can the IT staff recover backup data files and media?
- Process: What is the order of recovery? Bring up internal databases and communications first and external servers (email and web site) be reestablished later? What are the recovery time standards for the company to regain business operations? What is acceptable? What is not acceptable?
- Technology: Are there adequate numbers of back up devices for critical systems? Can third-party service providers assist in recovering lost or damaged data?
6. User Response
- People: Can employees safely return to an operational state?
- Process: Does the company need to control access to services to select individuals first (e.g., finance, logistics, etc.)
- Technology: Can technology resolve immediate problems from the recovery vice the employee such as, for example, re-selecting printers and other data connections?

Twenty-two years of military service. Support for Government and Department of Defense (DOD) and Intelligence Community (IC) as a contractor; Information Systems Security Manager, Information Systems Security Officer, Security Certification Assessor, and Security Analyst. Provided cybersecurity experience with the following frameworks and guidance documents: DCID 6/3, ICD 503, and Risk Management Framework (RMF). Contractor with: The Analytical Science Corporation (TASC), Systems High Corporation (SHC), and Mantech International Corporation on Chantilly, VA.