Is “Agile” Cybersecurity Possible?

NIST Frameworks that Fit
In the age of lean and agile development, can “Agile Cybersecurity” fit into these paradigms? Is it possible to take the complexity of security controls and measures from the varied National Institute of Standards and Technology’s (NIST) frameworks to keep pace with the demands for agility? We will suggest it is possible. If we determine, based upon the current mainstream direction from NIST to establish such standards, a hybrid solution is necessitated for any of the several candidate frameworks discussed based upon the industry involved.
Considering the strengths and weaknesses of the “agile” versus the “non-agile” cybersecurity frameworks, agile is a certain possibility. While NIST 800-53, revision 4, “Security and Privacy Controls for Federal Information Systems and Organizations”[1], specifically, is a cumbersome and bottom-driven approach to cybersecurity, it has its own distinct advantages and disadvantages. It requires from four to six months of active implementation and review to reach the desired state of an issued Authority to Operate (ATO) by a designated Authorization Official (AO). It further assumes a voluminous number of security and privacy controls that can reach from 400 to 800 controls. This further contributes to NIST 800-53 and its struggle to remain relevant.[2] Even worse is that NIST as of 2018 is on a path to release NIST 800-53 revision 5 as another “global” means to protect the nation’s critical infrastructures with no consideration of the demands it will place on the nation’s industries.
We need to specifically consider the advent of the National Cybersecurity Framework (NCF), NIST 800-171, the System Administration, Audit, Network and Security (SANS) Institute (a non-NIST based) solution and the Health Insurance Portability and Accountability Act (HIPAA) as the most likely to inject agility to the system and software development processes. These are the major candidates most likely to ensure solid cybersecurity protections and meet the rapidity called for by agile development; the hope lies with these faster-moving solutions than NIST 800-53.
These frameworks and their associated strengths can be contrasted to NIST 800-53. These “agile” approaches have a defined set of top-down and global controls that affords actual simplicity that may in fact be where cybersecurity must go to remain viable. These controls more easily address and limit the major risks and threats affecting the cybersecurity environment across the nation and the globe; while not as all-encompassing as NIST 800-53, the immediate solutions rest with these four major approaches depending in part to their unique IT environments.[3]
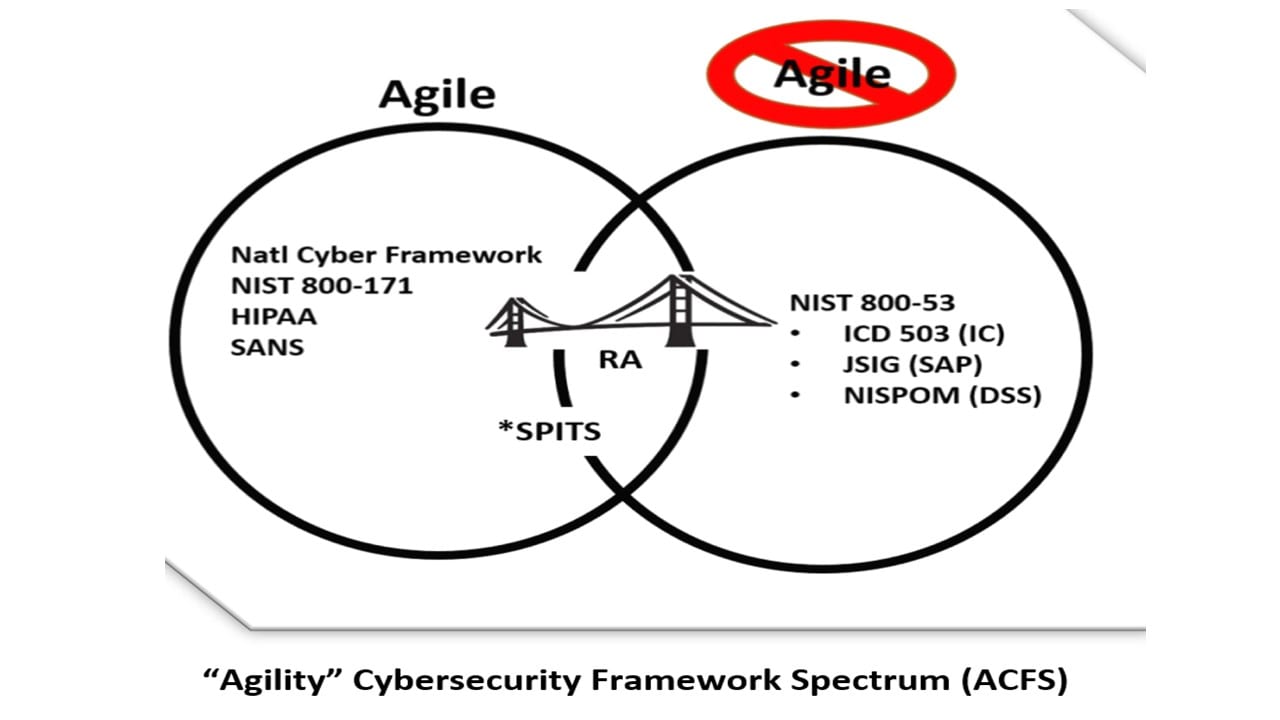
Viewing the advantages of each side of the “Agility” Cybersecurity Framework Spectrum (ACFS) (above), the real agility lies with the simplicity and more specifically, the constrained number of controls on the left side of the ACFS Venn diagram. It provides the broadest solution for disparate IT systems and environments. NCF, for example, and its brethren frameworks, are ideal to describe an agile environment and to address software release/version updates in much shorter time frames.
Furthermore, the importance and role of the Risk Assessment (RA) affords an overall “bridge” to inject even greater agility to current cybersecurity processes. For example, in comparison with NIST 800-53, NCF, NIST 800-171, and the SANS solutions are far faster to implement than the traditional 800-53 framework. The RA offers even a faster mechanism already an inherent control derived from NIST 800-53.
SEE NEXT MONTH’S BLOG POST: “More About the Risk Assessment and the Introduction of the Specialized Information Technology System (SPITS)”
——————————————————————————————————————–
[1] NIST 800-53 revision 5 is currently in draft. When finally released, it will remove the word “federal” to denote its applicability by companies, agencies, and organizations not US federal entities.
[2]A criticism of NIST 800-series is that they tell you “what” to do, but not “how” to do them. This book is a first-of-its-kind how-to book designed to support companies, agencies and their IT staffs implement and better protect vital data.
[3] For example, HIPAA was created around the protection of Personal Health Information (PHI) and is mandated under federal law as the requited framework specific to the defined “covered entities.”
Current Resource Available on Amazon:

Ms. Columbus has worked in the Intelligence Community (IC) for over 20 years. She retired from the US Air Force in 2014 after working as a Senior Advisor providing authoritative advice on all aspects of Cyberspace operations, force structure and organizational concepts. She oversaw strategic support activities to enable the right mix of cyber capabilities for future operations.










