Cyber Threat Hunting (CTH) in an Age of Escalating Cyber Threats

Why Cyber Threat Hunting?
As the digital world evolves and grows, so do the complexities and challenges of cybersecurity. Cyber Threat Hunting (CTH) is an essential component of a robust cybersecurity strategy, helping organizations actively defend their data and systems by searching for, identifying, and eliminating cyber threats. This book explores the importance of CTH and alignment with creating an active-passive defense posture to detect, fix, and stop cyber threats.
The Role of Cyber Threat Hunting
CTH involves proactively and iteratively searching through networks and datasets to detect and isolate advanced threats that evade existing automated security solutions (Scarfone & Mell, 2012). This process requires a high degree of knowledge about network infrastructure, a solid understanding of how the threat actors operate, and expertise in various hunting tools and techniques.
Importance of Cyber Threat Hunting
The growing sophistication and frequency of cyberattacks demonstrate the importance of cyber threat hunting. Reactive security measures like firewalls, intrusion detection systems (IDS), and antivirus software are essential but insufficient as they primarily defend against known threats (Ahlber, 2016). As attackers increasingly utilize new, unseen methods, proactive approaches become necessary. CTH allows organizations to discover and mitigate novel threats preemptively, reducing their potential impact (Lee, Lee, Kim, & Kim, 2018).
Cyber Threat Hunting and Active Passive Defense
The alignment of CTH with active defense postures is integral in modern cybersecurity strategies. Active defense refers to defending networks by actively searching for threats and reacting swiftly (Stiawan, et al., 2018) Integrating CTH into an active-passive defense strategy enhances an organization’s ability to detect threats early, allowing for rapid response and mitigation before damage occurs (Pash, 2017). Moreover, it allows organizations to learn from previous attacks, continually improving their defenses and readiness for future threats.
The cybersecurity landscape is dynamic, with threat actors continually innovating their tactics. To stay ahead, organizations must embrace proactive measures like CTH. Through the iterative process of hunting threats, organizations can effectively build an active security posture to defeat cyber threats ultimately.
The Cybersecurity Threat Hunt Process (THP)–The Tactical Piece
Expanding Cyber Threat Hunting: The Advent of Cyber Threat Hunting 2.0
As cyber threats evolve, so must the strategies and methodologies to counter them. CTH 2.0 expands on the original 2019 framework of CTH to add a fifth critical element: the Deconfliction Cell. Furthermore, it specifies the 2019 Cybersecurity Threat Hunting Process (C-THP) concept, and it expands to five elements: Indicators and Warning, Cyber Threat Intelligence, Incident Response, the Cyber Threat Hunt Team, and the Deconfliction Cell.
This new CTH Process 2.0 [1] (CTHP) is inherently cyclic and iterative in nature, fostering an efficient feedback loop that continually refines its efficacy over time. The process initiates with the Indicators and Warning (I&W) cell, which leverages advanced data analytics tools to sift through massive data sets and detect potential cyber threats. These findings are then passed to the deconfliction cell, which works diligently to distinguish between genuine threats and false positives, thus preventing the unnecessary allocation of resources to benign entities.
Once threats are confirmed, the Cyber Threat Intelligence (CTI) team delves deeper into the analysis, conducting detailed forensic investigations to determine the threats’ nature, source, and potential impact. They decipher whether anomalies and irregularities indicate the presence of a malicious actor within the network. Concurrently, the Incident Response (IR) team is alerted, taking swift action to shield the internal workings of the network and mitigate the potential damage.
Leadership is essential in guiding the overall threat-hunting process, establishing the strategy, fostering a proactive defense posture, and ensuring effective team communication. This book examines how and why leadership is crucial in threat hunting, primarily when Cyber Threat Intelligence (CTI) identifies a reportable incident requiring response and reporting (Chen, 2014). A well-defined leadership structure provides strategic guidance, promoting a proactive rather than a reactive approach to cybersecurity. Leaders drive the creation and implementation of a comprehensive cyber threat-hunting process, including indicators and warnings, threat intelligence, and incident response (Shackelford, 2016).
After CTI identifies a significant incident, leadership is critical in coordinating an appropriate and timely response. It ensures that reportable incidents are communicated effectively within the organization and to external stakeholders as necessary. Furthermore, leadership ensures that decisions in response to the incident align with the organization’s cybersecurity strategy (Karanja, 2020). Leadership’s role extends to the Incident Response (IR) phase. It is the main entry point where leadership begins to exert directed action against threats to its infrastructures and data, where they must ensure effective coordination between the various teams involved. This could involve decision-making related to isolating systems, initiating recovery actions, or even public communications if the incident has a broader impact (ISO/IEC 27035, 2016).
Leadership
Effective leadership is the cornerstone of a successful threat-hunting process, from the early stages of threat detection to incident response and recovery. Through a strategic and coordinated approach, leadership can drive proactive threat hunting, ensuring the organization remains resilient in the face of evolving cyber threats.
Finally, to counteract the threats, the Cyber Threat Hunt Teams adopt a more aggressive stance, based on leadership’s direction and guidance, taking decisive actions to deter or eliminate threats within the network. Notably, the process continues; the findings and insights from these actions are funneled back into the CTHP. Lessons learned help fine-tune the process, improving the efficiency of I&W detection mechanisms, the accuracy of deconfliction, and the targeted response of both CTI and Cyber Threat Hunt Teams. This cyclical nature of the CTHP underscores its adaptability, resilience, and capacity for continuous learning and improvement in the face of evolving cyber threats.
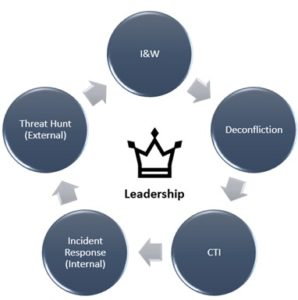
CTH 2.0 Major Participants
The Indicators and Warning (I&W) Cell
In the context of CTH2.0, indicators and warnings serve as the first line of detection, alerting the organization to potential threats (Borg, 2017). These include anomalous network behavior, unexpected data transfers, or unusual access patterns. By enhancing detection capabilities and combining them with advanced artificial intelligence and machine learning tools, the sensitivity and specificity of these indicators can be improved significantly (Azaria, 2019).
In the contemporary cybersecurity landscape, the Indicators and Warning (I&W) cell’s role has become increasingly critical against cyber threats (Borg, 2017). This book further discusses how I&W uses data science tools to detect the unknown-unknowns of the dearth of cyber threats globally, thus effectively managing limited resources for Cyber Threat Intelligence analysts and Cyber Threat Hunt Teams under the CTH 2.0 framework (Froehlich, 2020). The I&W cell sifts through large volumes of information, data, message, and security logs, searching for potential threats (Azaria, 2019). Their goal is to identify the unknown-unknowns of cyber threats, i.e., the threats that are not yet known to the organization or the global cybersecurity defense community (Grigg, 2020).
With the I&W cell identifying potential threats, the Cyber Threat Intelligence analysts and Cyber Threat Hunt Teams can focus on specific targets, avoiding unnecessary or spurious ones. This streamlining of resources not only boosts the effectiveness of threat hunting but also aids in mitigating potential threats more quickly and efficiently (Maurushat, 2019).
Data science tools and methodologies are instrumental in handling the vast amounts of data generated in the cybersecurity landscape. They help identify patterns, detect anomalies, and anticipate potential threats, making them indispensable for the I&W cell (Zikopoulos & Eaton, 2011). Finally, the I&W cell plays a pivotal role in the CTH2.0 framework, aiding in the early detection of threats and effectively managing resources for other cybersecurity teams. Leveraging data science tools, it helps organizations stay one step ahead in the rapidly evolving cybersecurity landscape.
Cyber Threat Intelligence (CTI)
The role of CTI is to provide information about potential or existing threats based on the analysis of threat data. It allows the threat-hunting team to understand the threat landscape, identify potential attack vectors, and proactively guard against them (Grigg, 2020). In the upgraded process, CTI is tasked with identifying threats, strategizing, and planning preemptive measures, ensuring a proactive stance against threats.
The Incident Response (IR) Team
A surge in the complexity and frequency of cyber threats has paralleled the accelerating digital transformation. An essential part of mitigating this risk lies in an entity’s Incident Response (IR) Team, which is charged with preventing, managing, and recovering from cybersecurity incidents (ISO/IEC 27035, 2016). The primary responsibility of the IR Team is to prepare for, respond to, and recover from cybersecurity incidents that could compromise an entity’s IT infrastructure and data. Their duties include developing incident response plans, conducting forensic analysis, and recovering systems after an attack (Karanja, 2020).
The activities of an IR Team can be broken down into the incident response lifecycle: Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned, each phase having its distinct role in the overarching cybersecurity strategy (ISO/IEC 27035, 2016). The preparation phase involves developing a comprehensive incident response plan, establishing communication protocols, and providing personnel training (Ahmad, 2018). This phase is crucial for preventing potential cybersecurity incidents and ensuring the team is ready to respond efficiently when incidents do occur. In the identification phase, the IR Team detects and analyzes cybersecurity incidents, assessing their potential impact on the IT infrastructure and data (Ahmad, 2018). This phase involves close collaboration with other teams, such as the Indicators and Warning (I&W) cell and the Cyber Threat Intelligence (CTI) team.
During these phases, the IR Team’s role is to contain the incident to prevent further damage, eradicate the threat from the system, and recover the affected systems or data. These activities often involve technical tasks such as system isolation, malware removal, and system restoration (Karanja, 2020). The final phase involves reviewing the incident, determining its cause, assessing the effectiveness of the response, and identifying areas for improvement. Insights from this phase feed back into the preparation phase, enhancing the organization’s overall cybersecurity posture (ISO/IEC 27035, 2016).
The Cyber Threat Hunt Team
The Cyber Threat Hunt Team is responsible for actively searching for, identifying, and eliminating threats in the network. The hunt team’s role expands beyond active and passive defense into strategy formulation, using insights from CTI to inform threat mitigation strategies. Their collaboration with the organization’s Incident Response (IR) team and CTI analysts is further enhanced, improving the overall efficiency and effectiveness of the hunting process (Maurushat, 2019).
The Deconfliction Cell
The advent of the Deconfliction Cell is the cornerstone of the CTH2.0 concept. The cell operates across agencies to assess whether a detected threat is an inadvertent friendly element. This reduces the risk of misinterpreting internal activities as external threats, minimizing unnecessary system lockdowns and investigations, and fostering efficiency in threat response activities (Froehlich, 2020).
In recent years, threat hunting has been embraced as a proactive security measure to counter the increasing sophistication of cyber threats (Ahlberg, 2016). However, distinguishing between actual threats and benign activities poses a challenge, often resulting in false positives that degrade effectiveness. This book underlines the importance of threat signature deconfliction in mitigating such issues (Borg, 2017).
False positives in cybersecurity refer to benign or friendly activities incorrectly flagged as potential threats by cybersecurity systems. These can lead to wasted resources, unnecessary alerts, and potential desensitization to genuine threats (Levesque, 2018). An overloaded system with false positives may overlook actual threats, negatively impacting the overall security posture of an organization. Threat signature deconfliction refers to distinguishing between genuine threats and benign activities. By correctly identifying and filtering out friendly activities from the threat landscape, deconfliction improves the effectiveness of cyber threat-hunting activities (Froehlich, 2020). Furthermore, threat signature deconfliction enhances detection accuracy and reduces the burden on cybersecurity systems and personnel. Eliminating false positives allows organizations to focus their resources on genuine threats, improving response times and overall cybersecurity efficacy (Azaria, 2019).
Several case studies exemplify the effectiveness of threat signature deconfliction in reducing false positives. These include organizations in the financial sector, healthcare, and government agencies, which have significantly benefited from incorporating deconfliction strategies into their cybersecurity measures (Grigg, 2020).
In the rapidly evolving cybersecurity landscape, threat signature deconfliction is critical in ensuring the effectiveness of threat-hunting activities. Reducing false positives allows organizations to focus on countering threats, enhancing security posture, and protecting valuable assets.
Conclusion
The C-THP is a collaborative activity with the organization’s Incident Response (IR) team, an internal defensive organizational team designed to respond to attacks against internal architecture and conduct appropriate forensic activities as required. This process includes the Deconfliction Cell, thus refining the original 2019 CTH process. The IR team determines whether an event should be presented as an actual incident for a timely response by the Hunting Team as well, in coordination with assigned CTI analysts and the Deconfliction Cell, and most importantly, with organizational Leadership who are charged with making decisions during occurrences, events, or actual threat incidents. CTH2.0 is the comprehensive and advanced methodology for managing cyber threats. It fosters a proactive approach to cyber defense, making it more effective in identifying, mitigating, and eliminating threats.
References
Ahlberg, J. (2016). Cyber Threat Hunting. SANS Institute InfoSec Reading Room
Ahmad, A. (2018). The Role of Incident Response Teams in Cyber Security: A Review. International Journal of Security and Its Applications, 12(1), 1-14.
Azaria, A. (2019). Data Science in Cybersecurity: Harnessing the Power of Machine Learning. Cybersecurity Review Journal, 4(2), 1-10.
Borg, M. (2017). Deconfliction: A Critical Factor in Modern Cybersecurity. Information & Security: An International Journal, 38(1), 45-58.
Chen, P., Desmet, L., & Huygens, C. (2014). A study on advanced persistent threats. IFIP International Conference on Communications and Multimedia Security. Springer, Berlin, Heidelberg.
Froehlich, B. (2020). Deconfliction in Cyberspace: An Essential Mechanism for Avoiding Friendly Fire. Journal of Cyber Policy, 5(1), 64-77.
Grigg, K. (2020). Cyber Threat Hunting: Leveraging the Indicators and Warning Cell. Incident Response Journal, 3(1), 17-25.
ISO/IEC 27035:2016. (2016). Information technology — Security techniques — Information security incident management. International Organization for Standardization.
Karanja, E. (2020). Role of an Incident Response Team in Cybersecurity. Journal of Cybersecurity and Information Management, 4(1), 10-24.
Karanja, E. (2020). Role of Leadership in Cybersecurity: A Review. Journal of Cybersecurity and Information Management, 4(1), 10-24.
Lee, S., Lee, K., Kim, P., & Kim, D. (2018). Cyber Threat Intelligence Model for Cyber Threat Hunting. Future Internet, 10(7), 60.
Levesque, J. (2018). The Impact of False Positives on Cybersecurity Effectiveness. Cybersecurity Trends, 2(3), 15-29.
Maurushat, A. (2019). Streamlining Resources in Cyber Threat Hunting. Computer Law & Security Review, 35(2), 105-120.
Maurushat, A. (2019). The role and challenges of the cyber threat hunt team in active defence: An international legal and practical perspective. Computer Law & Security Review, 35(2), 105-120.
Pash, C. (2017). Hunting for Hidden Threats: Incorporating Threat Hunting into Your Security Strategy. Security Intelligence.
Scarfone, K., & Mell, P. (2012). Guide to Intrusion Detection and Prevention Systems (IDPS). National Institute of Standards and Technology Special Publication 800-94.
Shackelford, S. (2016). Making sense of cybersecurity: Toward a theory of cyber peace. Georgetown Journal of International Affairs, 17(2), 109-123.
Stiawan, D., Idris, Y., & Yazid, I. (2018). Cyber Threat Intelligence Framework and Analytics: A survey. Journal of Network and Computer Applications, 117, 42–55.
Zikopoulos, P., & Eaton, C. (2011). Understanding Big Data: Analytics for Enterprise Class Hadoop and Streaming Data. McGraw-Hill Osborne Media.
[1] For this paper, CTH and CTHP may be used interchangeably to describe this next generation of Threat Hunting.

Dr. Russo is currently the Senior Data Scientist with Cybersenetinel AI in Washington, DC. He is a former Senior Information Security Engineer within the Department of Defense’s (DOD) F-35 Joint Strike Fighter program. He has an extensive background in cybersecurity and is an expert in the Risk Management Framework (RMF) and DOD Instruction 8510, which implement RMF throughout the DOD and the federal government. He holds a Certified Information Systems Security Professional (CISSP) certification and a CISSP in information security architecture (ISSAP). He has a 2017 Chief Information Security Officer (CISO) certification from the National Defense University, Washington, DC. Dr. Russo retired from the US Army Reserves in 2012 as a Senior Intelligence Officer.









