TOP 10: Cybersecurity Policies (NIST)

How to Demonstrate a Strong Security Posture
A continuing focus on the third-leg of of the cyber-Body of Evidence (BOE), the Cybersecurity Policy/Procedure. ~Mark

You, your business, or agency have decided to tackle the challenges of a National Institute of Standards and Technology (NIST) framework calling for a multitude of cybersecurity policies. These policies will form a major portion of your Body of Evidence (BOE) to the government, Contract Officer, etc., that will demonstrate you have a secure Information Technology (IT) environment. These are the Top 10 policies needed to begin.
These 10 are selected to truly demonstrate compliance and meeting a little understood NIST requirement of “adequate security.”
The Top 10 are:
1. Access Control (AC) Policy. (AC Family)
Identify the types of users and what level of access they are authorized. Typically, there are general users who have regular daily access to the corporate system data, and elevated/privileged users. Elevated/privileged users are limited to, for example, System Administrators (SA), Database Administrators (DBA), and other designated Help Desk IT support staff personnel who manage the back-office care of the system; these users may also have root access.
Root access provides what is more typically described as super-user access. These individuals should be highly and regularly security screened. These individuals need to be regularly assessed or audited by senior corporate and third-party security personnel and agencies.
AN EXAMPLE POLICY PARAGRAPH: The company has defined two types of authorized users. There are general users, those that require normal daily access to company automated resources, and privileged users, employees with elevated privileges required to conduct regular back-office care and maintenance of corporate assets and IT systems. Access to the company’s [example] financial, ordering, and human resource systems will be restricted to those general users with a need, based upon their duties, to access these systems. Immediate supervisors will validate their need and advise the IT Help Desk to issue appropriate access credentials [login identification and password] after completing “Cybersecurity Awareness Training.” User credentials will not be shared and….”
EXAMPLE 2: Non-privileged users are prohibited from executing any privileged functions or system audits without the authority of the company’s Chief Operating Officer, Chief Information Security Officer, or their designated representative. All requests will be submitted in writing with their first-line supervisor validating the need for such access for a limited and specified time.
2. Separation of Duties Policy. (Related to Access Control Family [AC]).
This should be described in the policy document and should identify roles and responsibilities of how oversight will be executed. Also, individuals should be assigned in-writing specific to their roles and responsibilities. This would also include the reporting thresholds of unauthorized activities and who is alerted to internal threats.
3. Remote Access Policy. (Related to Access Control Family [AC]).
This control is about remote access where one computer can control another computer over the Internet. This may include desktop support personnel “remoting into” an employee’s computer to update the latest version of Firefox ® or a work-at-home employee inputting financial data into the corporate finance system. Identify these types of access as part of a guide and describe who is authorized, how their access is limited (such as a finance employee can’t issue themselves a corporate check), and the repercussions of violating the policy.
4. Acceptable Use Policy (AUP) . (Related to Access Control Family [AC]).
The AUP would include defining the types and kinds of sites restricted from access by employees. These are typically gambling, pornography sites, etc. The AUP should be reviewed by a lawyer before requiring employees to sign. This would also include wireless access agreements.
5. Auditing (AU) and Log Review Policy. (AU Family).
The AU control is primarily about the ability of the system owner/company to monitor unauthorized access to the system through system logging functions of the Operating System and other network devices such as firewalls. A SA is typically assigned the duty to review log files; these may include both authorized and unauthorized access to the network, applications, databases, financial systems, etc.
Most businesses will rely on manual review; however, some “smart” servers and firewalls can provide automated alerts to IT personnel of unauthorized use or intrusion. The key is to understand the auditing capabilities of the IT system and be prepared to defend its capabilities and limitations if government representatives or third-party assessors request proof of control compliance.
6. Configuration Management (CM)/ Configuration Control Board Policy. (CM Family)
CM requires establishing baselines for tracking, controlling, and managing a business’s internal IT infrastructure. An effective CM policy needs to consider information security implications for the development and operation of information systems. This will include the active management of changes to company hardware, software, and documentation.
Also, effective CM of information systems requires the integration of the management of secure configurations into the CM process. If good CM exists as a well-defined “change” process, protection of the IT environment is more assured.
7. Patch Management Policy. (Configuration Management [CM] Family).
This policy establishes the “battle rhythm” for the review and update of key application, operating, and security patch cycles. Much of this can be automated, but a written policy ensures an organization’s ability to ensure continuity of the overall CM effort.
8. Security Impact Assessment Policy. (Configuration Management [CM] Family)
Analysis should look at any change to the architecture, be it changes in hardware, software, firmware, or architecture. This should be described in the corporate CM process and should be a formal and maintained write-up from a member of the IT team, for example, that the change will or will not have a security impact, and it may or may not be security relevant.
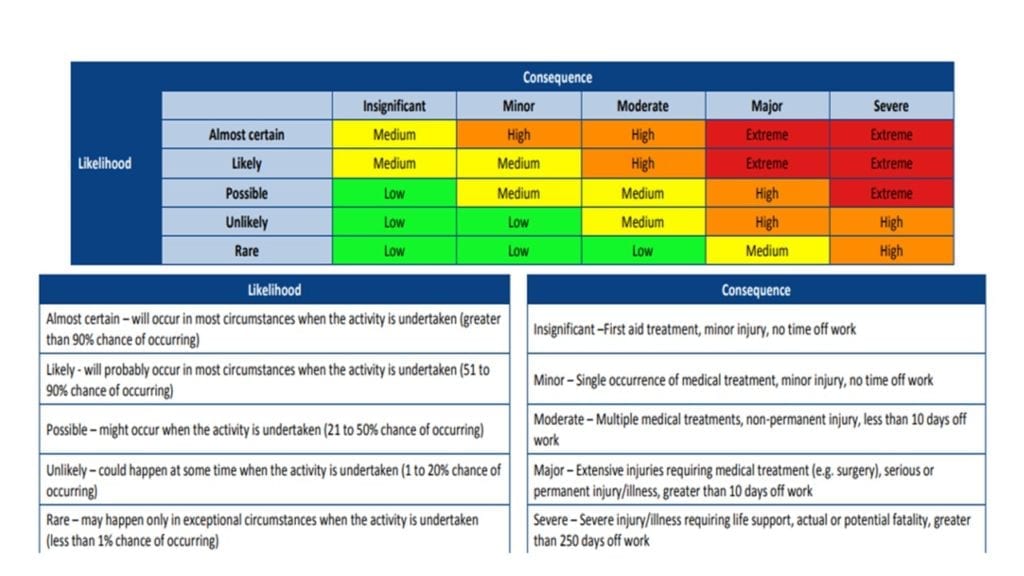
If the change introduces a “negative” impact, such as eliminating backup capabilities or introducing currently unsupportable software (possibly due to funding constraints). A Risk Matrix or Register should be maintained to identify qualitative likelihoods of vulnerabilities to the system (See Below).
9. Incident Response (IR) Policy. (IR Family)
Incident Response (IR) primarily requires a plan, an identification of who or what agency is notified when a breach has occurred and testing of the plan over time. This control requires the development of an Incident Response Plan (IRP).
The first effort should be identifying what constitutes a reportable event that formally becomes an incident. This could include a confirmed breach that has occurred to the IT infrastructure. Incidents could include anything from a Denial of Service (DOS) attack—an overloading of outwardly facing web or mail servers–or exfiltration of data—where corporate data, for example, has been copied or moved to outside of the company’s firewall/perimeter. Incidents could also include the destruction of data that the company’s IT staff, for example, identifies through ongoing audit activities.
10. Media Protection (MP)/Handling Policy. (MP Family).
The MP control was written to handle the challenges of managing and protecting the computer media storage. This would include concerns about removable hard drives and especially the ability for a threat employ the use of a Universal Serial Bus (USB) “thumb drive.” While computer users are aware of the convenience of the thumb drive to help store, transfer, and maintain data, it is also a well-known threat vector where criminals and foreign threats can introduce serious malware and viruses into unsuspecting users’ computers.
MP is also about assurances by the business that proper destruction and sanitization of old storage devices has occurred. There are many instances where federal agencies have not implemented an effective sanitization process, and inadvertent disclosure of national security data has been released to the public. Cases include salvage companies discovering hard drives and disposed computers containing sensitive data, and, in several cases, national security classified information, has occurred.
Be especially mindful that the sanitization process requires high-grade industry or government-approved applications that completely and effectively destroys all data on the target drive. Other processes may include physical shredding of the drive or destruction methods that further prevent the reconstruction of any virtual data by unauthorized personnel.
Supply Chain Risk Management (SCRM) 2.0. It’s not just about IT products, it’s also about IT services as well

Dr. Russo is currently the Senior Data Scientist with Cybersenetinel AI in Washington, DC. He is a former Senior Information Security Engineer within the Department of Defense’s (DOD) F-35 Joint Strike Fighter program. He has an extensive background in cybersecurity and is an expert in the Risk Management Framework (RMF) and DOD Instruction 8510, which implement RMF throughout the DOD and the federal government. He holds a Certified Information Systems Security Professional (CISSP) certification and a CISSP in information security architecture (ISSAP). He has a 2017 Chief Information Security Officer (CISO) certification from the National Defense University, Washington, DC. Dr. Russo retired from the US Army Reserves in 2012 as a Senior Intelligence Officer.