GUIDE: The Threat Hunt Response Engagement & Action Team (THREAT)

The “Optimal” THREAT Task Organization
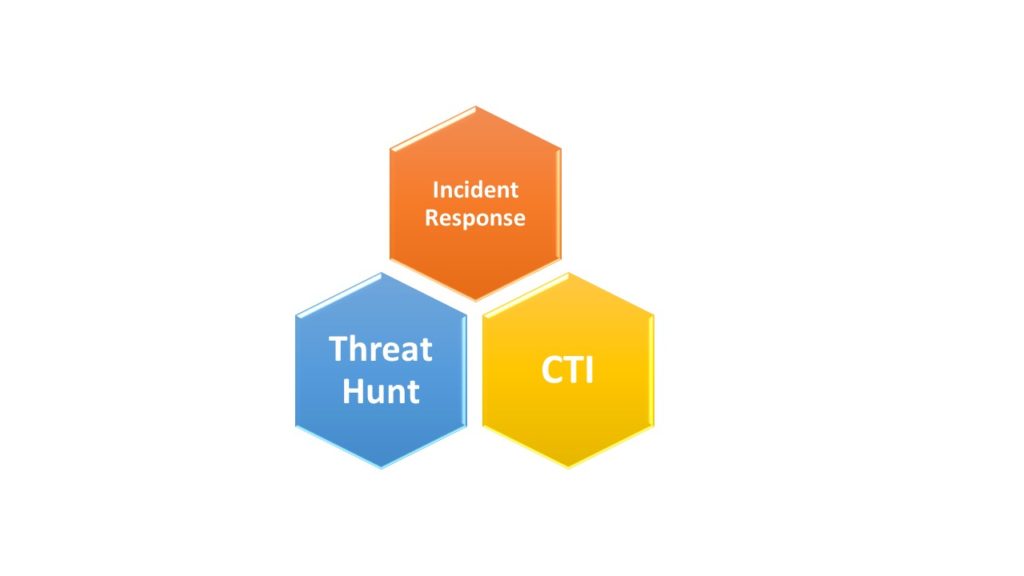
The most common question at this point of anyone looking at the Threat Hunt concept is what the correct number and types of individuals are needed to comprise the overall Threat Hunt team. A simple answer is the number should be at least 7. However, it will always depend too upon the agencies, companies, or industries’ priorities and resources. THREAT is the full active effort brought together to engage, mitigate, and preferably stop the cyber-threat in the respective IT environment. The task organization will depend on how the core triad of teams, Incident Response (IR), Cybersecurity Threat Intelligence (CTI), and Threat Hunt harmonize their roles. While senior leadership plays the most decisive role, IR is that entry into the Threat Hunt Process.
Threat Hunt Response Engagement & Action Team (THREAT)
The typical mix of skill sets are as outlined and described below. This is designed to be a guide for a company’s or agency’s leadership.
- Team Lead: This will be designated from within the Threat Hunt organization. This will be a senior leader who understands the rules and responsibilities of the overall Hunt effort. They will ensure that the THREAT effort is conducted in accordance with laws, rules, policies, etc., established by the federal and state governments, agencies, and organizations. They are the first-line of defense from improper use of THREAT in other than meeting the mission objectives of a specific Hunt activity.
- CTI Lead: This individual will be the liaison to the main CTI team. They will review current and past reports to identify anomalies, threat signatures, etc., and provide all pertinent information and intelligence to the team. Once the Hunt is completed, they will be responsible for creating reports to leadership, conducting After Action reporting activities, and updating the Master Hunt Threat Data Base (MHTDB).

- 3. Hunt Technician: This individual will have elevated system privileges in order to determine the nature of the cyber-threat. Their skill sets would include access to any Security Information Event Management (SIEM) devices or firewalls for updating policy settings, configurations, etc. This may include, for example, blacklisting or whitelisting actions by both identified threat and friendly actors. This should include the application and use of such tools as nmap, Wireshark, etc., for specific data packet inspection. The Hunt Tech may be supplemented by additional members of the team based upon the extensiveness of the attack.
- 4. Forensics Technician: This individual would review and monitor all past and current log activities to assist both CTI and the Hunt Tech to better understand the cyber-threats’ motives and actions. This information would be used to supplement the CTI effort to identify commonalities and differences between previously identified signature actions of the cyber-threat. This individual would also be responsible for collecting data to be transferred to Law Enforcement (LE), intelligence professionals, etc., based upon any future external actions implemented by the company or agency.
- 5. Counter-Intelligence (CI)/Counter-Cybersecurity Intelligence (CCI) Technician: This individual would typically be a member of CTI with a deeper understanding of what mechanisms are best to be employed prior, during, and after an attack. They would assist in better informing the overall THREAT effort of how to best mitigate against like threat cyber-actors. Their role may be combined with CTI based upon resourcing and priorities.
- 6. Network Engineer Technician (NET): This individual should be drawn from the general IT organization with a wide-ranging understanding of the overall network. They would have root level access capabilities and would further advise and support THREAT with advanced programming and scripting knowledge that may be needed during and after a cyber-attack.
- 7. Incident Response Liaison (IRL): The IRL will directly communicate any organizational concerns from senior leadership and ensure compliance with established rules and regulations. The IRL will assist in avoiding any reduction or damage to the THREAT’s explicit effort to protect the IT system, network, or environment. They would also coordinate with Human Resources and supervisors where the threat is internal and may require disciplinary or final legal action.
Additionally, the THREAT may be supplemented by matrix personnel such as:
- Legal
- Law enforcement
- Supervisor (insider threat)
- Third-party (outside) consultant SMEs
The effort of an effectively pre-planned task organization against a cyber-threat is always optimal and can never ensure the absolute best solution. It will require an agency to ascertain its priorities within its available budgeting for SMEs assigned to the THREAT. The objective is to have these specialists identified, and to have the right expertise ensuring their availability during an assault. This combination of experts would be established to ultimately reduce the overall damage to their respective IT environments.

Dr. Russo is currently the Senior Data Scientist with Cybersenetinel AI in Washington, DC. He is a former Senior Information Security Engineer within the Department of Defense’s (DOD) F-35 Joint Strike Fighter program. He has an extensive background in cybersecurity and is an expert in the Risk Management Framework (RMF) and DOD Instruction 8510, which implement RMF throughout the DOD and the federal government. He holds a Certified Information Systems Security Professional (CISSP) certification and a CISSP in information security architecture (ISSAP). He has a 2017 Chief Information Security Officer (CISO) certification from the National Defense University, Washington, DC. Dr. Russo retired from the US Army Reserves in 2012 as a Senior Intelligence Officer.