Where is DOD NIST 800-171 Implementation Going?

Expectations Beyond DOD
In late 2018, the expectation is that the United States (US) federal government will expand the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171, revision 1, Protecting Unclassified Information in Nonfederal Information Systems and Organizations cybersecurity technical publication will apply to the entirety of the federal government. It will most likely require that any company, business, or agency, supporting the US Government is fully compliant with NIST 800-171 no later than the date of contract award. The Federal Acquisition Regulation (FAR) Committee’s Case # 2017-016 had an original suspense date of March 2018; that date has come and went.
The latest and expected timeframe for any final decision has moved to an expected timeframe of November/December 2018. While it is possible that the Federal Acquisition Regulation (FAR) Committee may further delay NIST 800-171 implementation, this information is no less critical.
Will the National Cybersecurity Framework (NCF) be
–For future blog post
a head-to-head contender?
While NIST 800-series Cybersecurity publications tell a business “what” is required, they do not necessarily help in telling “how” to meet the 110 security control requirements. Furthermore, the number of security controls may further increase based upon the actual or perceived threat to a specified federal agency or the selection of additional controls directed by the agency’s respective Chief Information Officer (CIO) through any future contracts; companies will need to confirm control requirements with their respective Contract Office.
Implications
NIST 800-171 applies to prime and subcontractors. There are three core contractual obligations:
- “Adequately safeguard” Controlled Unclassified Information (CUI), and if working with the Department of Defense (DOD), Covered/Critical Defense Information (CDI).
- Provide timely cyber-incident reporting to the government when a IT network breach is identified; typically, within 72 hours or sooner.
- If operating with a Cloud Service Provider (CSP), “adequate” security needs to also must be demonstrated; usually in the form of a business-to-business contract or Service Level Agreement (SLA). This should demonstrate acceptable due diligence to government Contract Officers (CO).
“Adequate Security?”
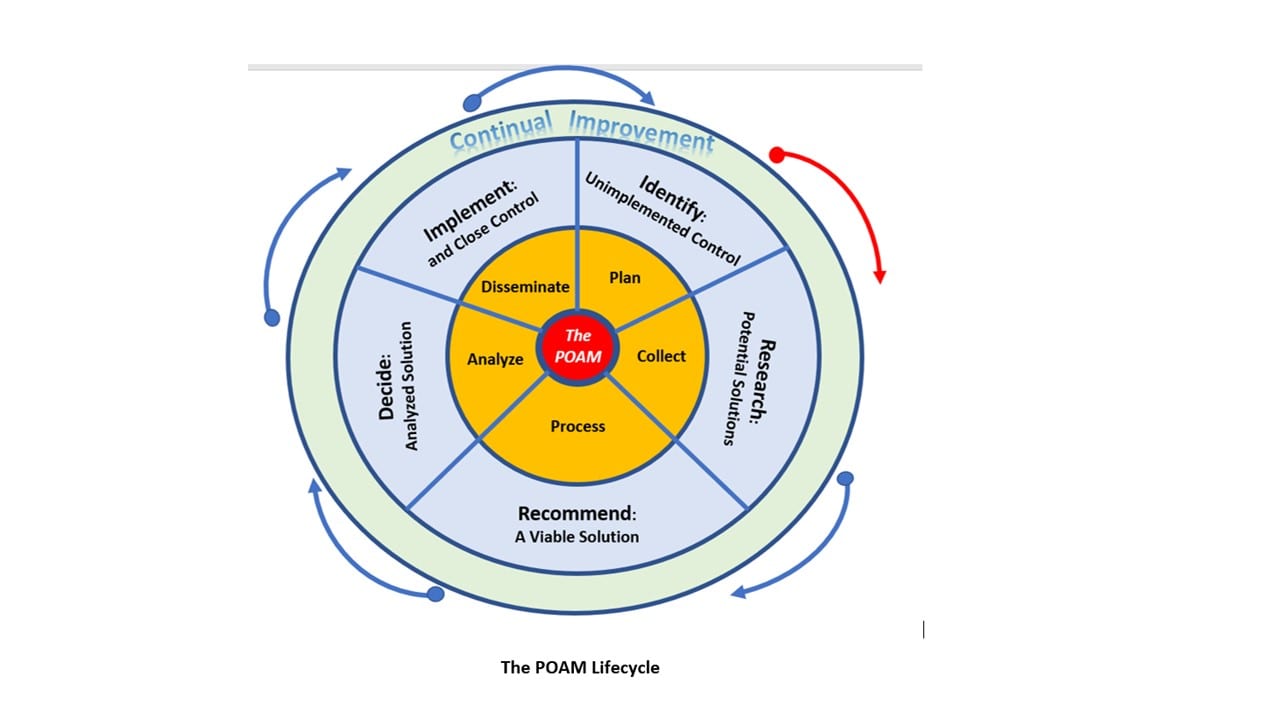
What is “adequate security?” Adequate security is defined by “compliance” with the 110 NIST 800-171 security controls, and when the business is issued the solicitation, i.e., contract award, or when authorized by the designated CO. This does not mean all security controls are in effect, but where a deviation is needed, it is sought by the business in coordination with the Contract Office. This will most likely come in the form of a Plan of Action and Milestones (POAM)[1]. A POAM is required as part of the official submission package to the government. It should identify why the company cannot currently address the control, and when it expects to resolve the control.
Additionally. the business is required to provide timely cyber-incident reporting to the government when a breach into its network has occurred. The DOD requirement, for example, is that the business notifies the government within 72 hours upon recognition of a security incident.
The US Government may require the business to notify cybersecurity support and response elements within the federal government. This may include the Department of Homeland Security’s (DHS) US Computer Emergency Response Team (US-CERT) (https://www.us-cert.gov/ ) or DOD’s CERT depending on what agency has oversight of the contract.
Changing federal cybersecurity contract requirements are also take into consideration the vast moves within the public and private sectors into cloud services. Typically, the security protections would be found in any contracts or Service Level Agreements (SLA) between the business and the CSP. These are normally sufficient evidence for the government. The good news is that there are many CSPs that are already in compliance with the government’s Federal Risk and Authorization Management Program (FedRAMP). Being FEDRAMP-compliant prior to final submission of the NIST 800-171 Body of Evidence (BOE) does, for example, help reduce the challenges of using an “external” or uncertified CSP.
Consequences of Non-compliance
There are several major consequences contractors and their subcontractors need to consider if either unable to meet or maintain their compliance. This can include several serious consequences and it is vital the business stays current regarding any changes or directions from the government that may jeopardize their business relationship with the government. These may include:
- Impact Future Contract Selection. This may be as basic as a temporary disbarment from federal contract work. It could also include permanent measures by government to suspend a company for a much longer time. Furthermore, the government could pursue the company for fraud or clear misrepresentation of their security posture to the US Government. This most likely would occur when an incident occurs within the businesses’ network, and a third-party government assessor determines there was willful disregard for NIST 800-171 and associated FAR/DFARS clauses.
- Remember, the business will always be assessed against the following criteria:
- Was there adequate security in place during the incident?
- Were the protections adequately established based upon a good-faith effort by the company to protect CUI/CDI?
- Assessments Initiated by the Government. At this phase, the Government will have unfettered access to determine culpability of the incident and whether it further brought harm against the government and its agencies. Cooperation is a key obligation and hiding the incident may have worse impacts than not reporting the intrusion.
- POAM will be required. The government will most likely mandate a POAM be developed to address the finding. This should be a good-faith effort to identify interim milestones with a final and planned completion date to ensure this situation will not occur again.
- Loss of Contract. Worse case, the Contract Officer or designated support element may determine that the company failed to meet the cybersecurity requirements and can chose to cancel the contract for cause.
What’s the minimum proof of a company’s cybersecurity posture?
The basis of NIST 800-171 is that contractors provide adequate security on all covered contractor Information Systems (IS). Typically, the minimum requirement to demonstrate control implementation is through documentation. Another term that is used throughout this book is an artifact. An artifact is any representation to a Contract Office or independent third-party assessor that shows compliance with specific security controls. It is a major part of the proof that a business owner would provide to the federal government.
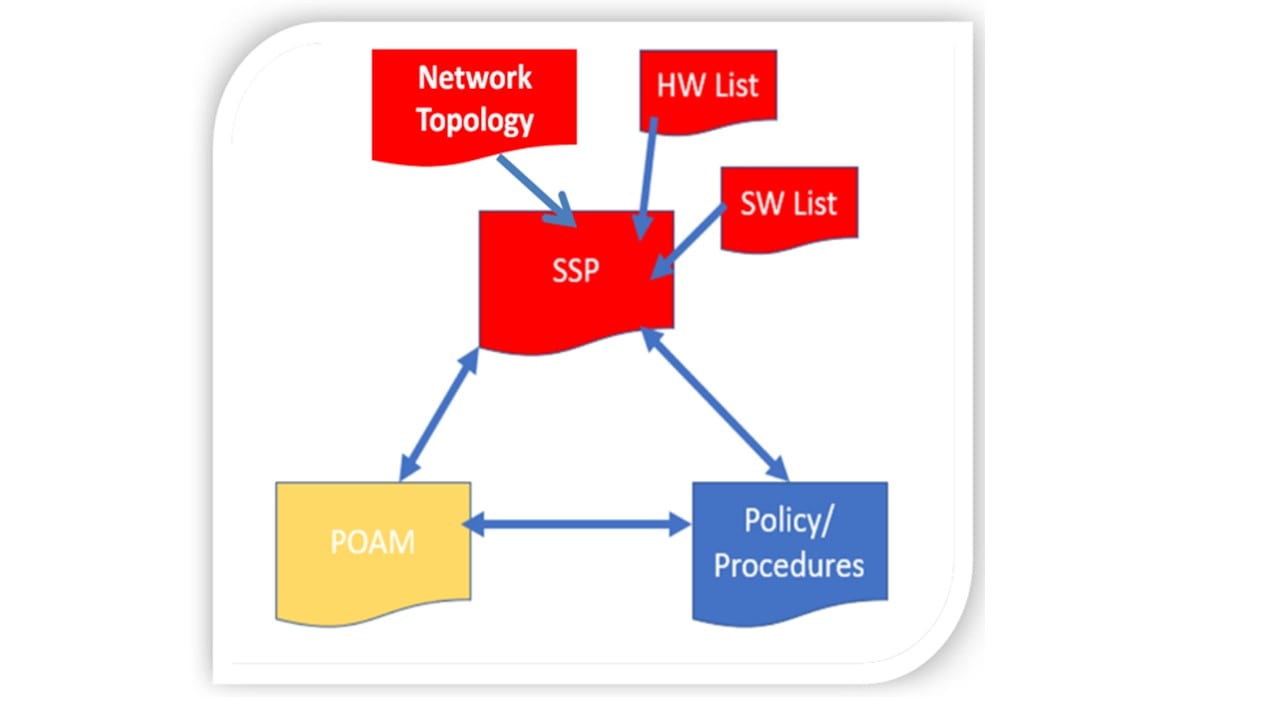
The common term for the collection of all applications and supporting artifacts is the Body of Evidence (BOE). The major items required for the BOE includes three major items:
- Procedure. Essentially any direction provided to internal employees and subcontractors that are enforceable under US labor laws and Human Resource (HR) direction. It is recommended that such a policy or procedure artifact be a singular collection of how the company addresses each of the 110 security controls.
All policy or procedure requirements are best captured in single business policy or procedure guide.
This should address the controls aligned with
the security control families
- System Security Plan (SSP). This is a standard cybersecurity document. It describes the company’s overall IT infrastructure to include hardware and software lists.
- Plan of Action and Milestones. This describes any control that the company cannot fix or fully demonstrate its full compliance. It provides an opportunity for a company to delay addressing a difficult to implement technical solution or because cost may be prohibitive.
POAMs should always have an expected completion date and defined interim milestones, if necessary, that describes the actions leading to a full resolution or implementation of the control. POAMs typically should not be for more than a year, however, a critical hint, a company can request an extension multiple times if unable to fully meet the control.
We have yet to receive any news regarding any FAR Committee announcements, and at this time it is likely any “global” decision of implementing NIST 800-171 beyond DOD is as of yet unclear.
Footnote
[1] Developing updates are discussing the requirement of a more streamlined POAM. A Plan of Action (POA) will most likely replace the more stringent federal guidance and direction for NIST-based POAMs for businesses and companies under these expected changes to NIST 800-171 and associated contract clauses’ modifications.
Two main resources available on Amazon
(images will take you to Amazon)

Dr. Russo is currently the Senior Data Scientist with Cybersenetinel AI in Washington, DC. He is a former Senior Information Security Engineer within the Department of Defense’s (DOD) F-35 Joint Strike Fighter program. He has an extensive background in cybersecurity and is an expert in the Risk Management Framework (RMF) and DOD Instruction 8510, which implement RMF throughout the DOD and the federal government. He holds a Certified Information Systems Security Professional (CISSP) certification and a CISSP in information security architecture (ISSAP). He has a 2017 Chief Information Security Officer (CISO) certification from the National Defense University, Washington, DC. Dr. Russo retired from the US Army Reserves in 2012 as a Senior Intelligence Officer.










