Continuous Monitoring: What Good Looks Like

Defining Continuous Monitoring
Cybersecurity is not about shortcuts. There are no easy solutions to years of leaders demurring their responsibility to address the growing threats in cyberspace. We hoped that the Office of Personnel Management (OPM) breach several years ago would herald the needed focus, energy and funding to quash the bad-guys. That has proven an empty hope where leaders have abrogated their responsibility to lead in cyberspace. The “holy grail” solution of Continuous Monitoring (ConMon) has been the most misunderstood solution where too many shortcuts are perpetrated by numerous federal agencies and the private sector to create an illusion of success. This article is specifically written to help leaders better understand what constitutes a true statement of: “we have continuous monitoring.” This is not about shortcuts. This is about education, training, and understanding at the highest leadership levels that cybersecurity is not a technical issue, but a leadership issue.
The Committee on National Security Systems defines ConMon as: “[t]he processes implemented to maintain current security status for one or more information systems on which the operational mission of the enterprise depends,” (CNSS, 2010). ConMon has been described as the holistic solution of end-to-end cybersecurity coverage and the answer to providing an effective global Risk Management (RM) solution. It promises the elimination of the 3-year recertification cycle that has been the bane of cybersecurity professionals.
For ConMon to become a reality for any agency, it must meet the measures and expectations as defined in National Institute of Standards and Technology (NIST) Special Publication (SP) 800-137, Information Security Continuous Monitoring for Federal Information Systems and Organizations. “Continuous monitoring has evolved as a best practice for managing risk on an ongoing basis,” (SANS Institute, 2016); it is an instrument that supports effective, continual, and recurring RM assurances. For any agency to truly espouse it has attained full ConMon compliance, it must be able to coordinate all the described major elements as found in NIST SP 800-137.
ConMon is not just the passive visibility pieces, but also includes the active efforts of vulnerability scanning, threat alert, reduction, mitigation, or elimination of a dynamic Information Technology (IT) environment. The Department of Homeland Security (DHS) has couched its approach to ConMon more holistically. Their program to protect government networks is more aptly called: “Continuous Diagnostics and Monitoring” or CDM and includes a need to react to an active network attacker. “The ability to make IT networks, end-points and applications visible; to identify malicious activity; and, to respond [emphasis added] immediately is critical to defending information systems and networks,” (Sann, 2016).
Another description of ConMon can be found in NIST’s CAESARS Framework Extension: An Enterprise Continuous Monitoring Technical Reference Model (Second Draft). It defines its essential characteristics within the concept of “Continuous Security Monitoring.” It is described as a “…risk management approach to Cybersecurity that maintains a picture of an organization’s security posture, provides visibility into assets, leverages use of automated data feeds, monitors effectiveness of security controls, and enables prioritization of remedies,” (NIST, 2012); it must demonstrate visibility, data feeds, measures of effectiveness and allow for solutions. It provides another description of what should be demonstrated to ensure full ConMon designation under the NIST standard.
The government’s Federal Risk and Authorization Management Program (Fed-RAMP) has defined similar ConMon goals. These objectives are all key outcomes of a successful ConMon implementation. Its “… goal[s]…[are] to provide: (i) operational visibility; (ii) annual self-attestations on security control implementations; (iii) managed change control; (iv) and attendance to incident response duties,” (GSA, 2012). These objectives, while not explicit to NIST SP 800-37, are well-aligned with the desires of an effective and complete solution.
RMF creates the structure and documentation needs of ConMon; it represents the specific implementation and oversight of Information Security (IS) within an IT environment. It supports the general activity of RM within an agency. (See Figure 1 below). The RMF “… describes a disciplined and structured process that integrates information security and risk management activities into the system development life cycle,” (NIST-B, 2011). RMF is the structure that both describes and relies upon ConMon as its risk oversight and effectiveness mechanism between IS and RM.
This article provides a conceptual framework to address how an agency would approach identifying a true ConMon solution. It discusses the additional need to align component requirements with the “11 Security Automation Domains” that are necessary to implement true ConMon. It is through the complete implementation and integration with the other described component that an organization can correctly state it has achieved ConMon.
Continuous Monitoring
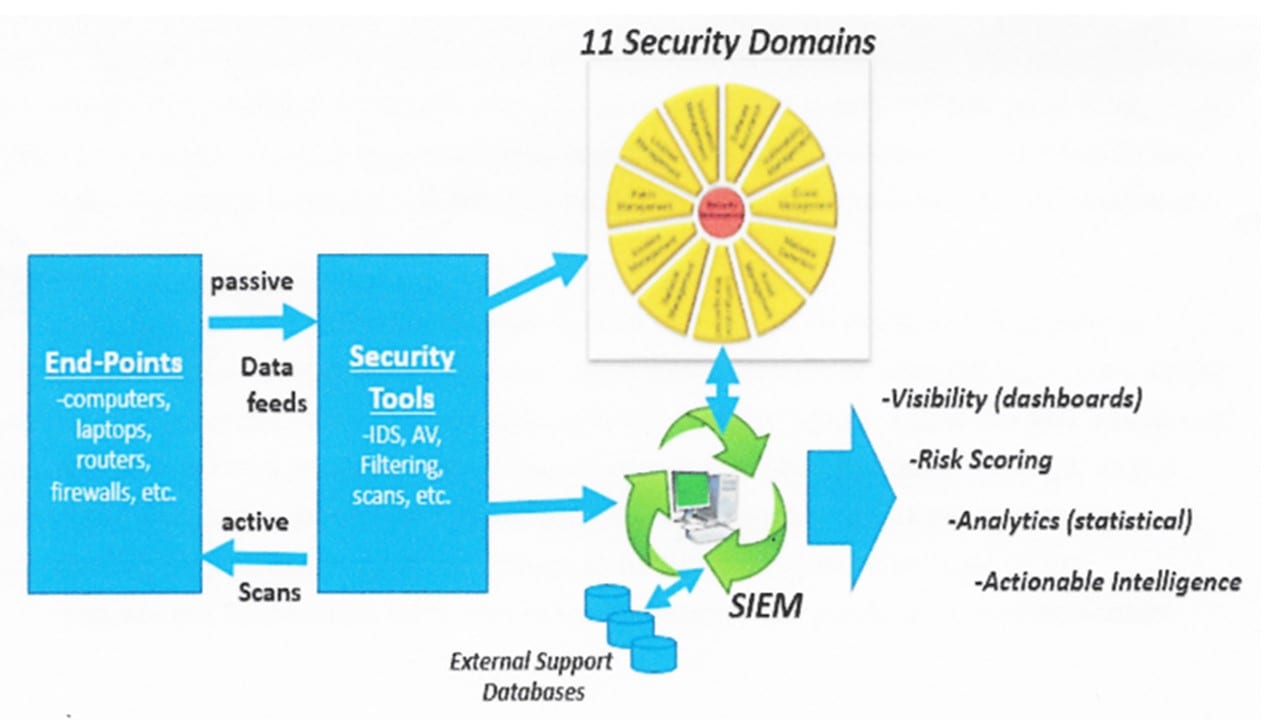
For ConMon to be effective and genuine, it must align end-point visibility with security monitoring tools. This includes security monitoring tools with connectivity to “end-points” such as laptops, desktops, servers, routers, firewalls, etc. Additionally, these must work with a highly integrated Security Information and Event Management (SIEM) device. The other “component” is a clear linkage between the end-points, security monitoring tools, and the SIEM appliance, working with the Security Automation Domains (See Figure Below). These would include, for example, the areas of malware detection, asset and event management. ConMon must first address these collective components to create a “First Generation” instantiation.
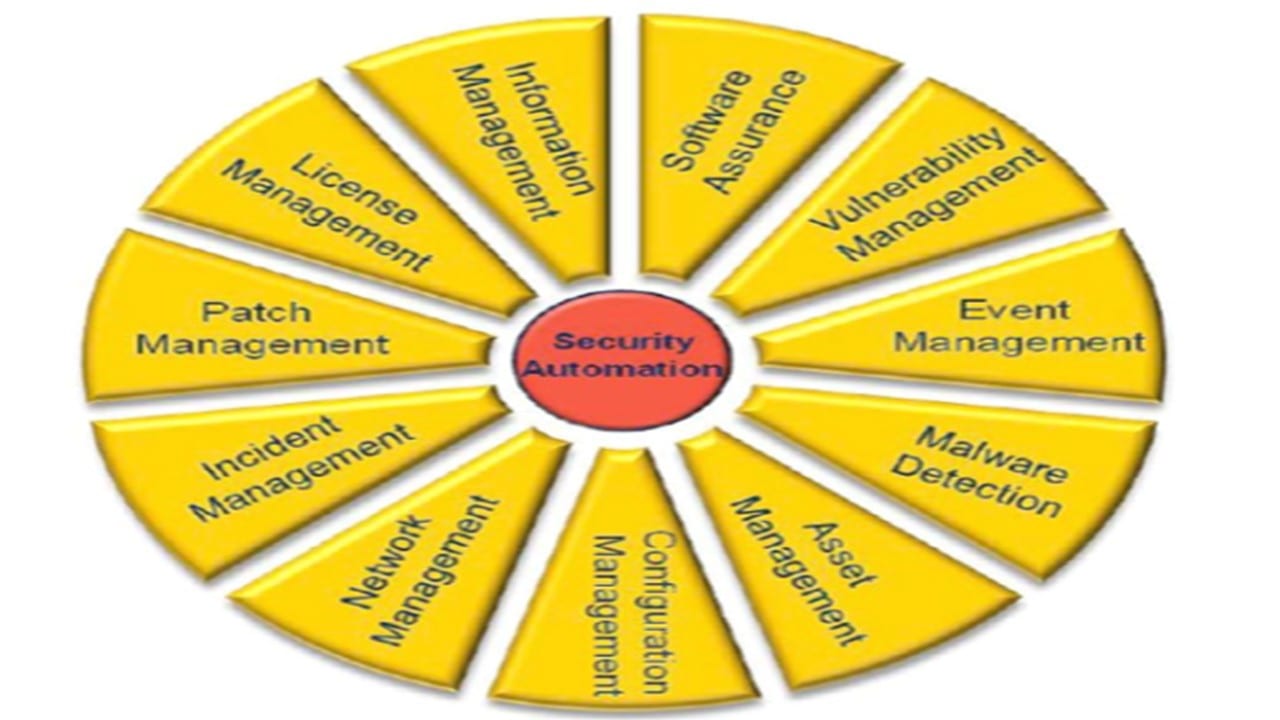
The 11 Security Automation Domains (NIST, 2011)
More specifically, a SIEM appliance provides the central core data processing capabilities to effectively coordinate all the inputs and outputs from across the IT enterprise. It manages the data integration and interpretation of all ConMon components. And, it provides the necessary visibility and intelligence for an active incident response capability.
End-point devices must be persistently visible to the applicable security devices. Together, these parts must align with the respective security controls as described in NIST SP 800-53. The selected SIEM tool must be able to accept these inputs and analyze them against defined security policy settings, recurring vulnerability scans, signature-based threats, and heuristic/activity-based analyses to ensure the environment’s security posture. The outputs of the SIEM must support the further visibility of the IT environment, conduct and disseminate vital intelligence, and alert leadership to any ongoing or imminent dangers. The expression above is designed to provide a conceptual representation of the cybersecurity professional attempting to ascertain effective ConMon implementation or to develop a complete ConMon answer for an agency or corporation.
Additionally, the SIEM must distribute data feeds in near-real time to analysts and key leaders. It provides for multi-level “dashboard” data streams and issues alert based upon prescribed policy settings. Once these base, First Generation functionalities are consistently aligning with the Security Automation Domains, then an organization or corporation can definitively express it meets the requirements of ConMon.
End-Points
It is necessary to identify hardware and software configuration items that must be known and constantly traceable before implementing ConMon within an enterprise IT environment. End-point visibility is not the hardware devices, but the baseline software of each hardware device on the network.
Configuration Management is also a foundational requirement for any organization’s security posture. Soundly implemented Configuration Management must be the basis of any complete CM implementation. At the beginning of any IS effort, cyber-professionals must know the current “as-is” hardware and software component state within the enterprise. End-points must be protected and monitored because they are the most valuable target for would-be hackers and cyber-thieves.
Configuration Management provides the baseline that establishes a means to identify potential compromise between the enterprise’s end-points and the requisite security tools. “Organizations with a robust and effective [Configuration Management] process need to consider information security implications concerning the development and operation of information systems including hardware, software, applications, and documentation,” (NIST-A, 2011).
The RMF requires the categorization of systems and data as high, moderate, or low regarding risk. The Federal Information Processing Standards (FIPS) Publication 199 methodology is typically used to establish data sensitivity levels in the federal government. FIPS 199 aids the cybersecurity professional in determining data protection standards of both end-points and the data stored in these respective parts. For example, a system that collects and retains sensitive data, such as financial information, requires a greater level of security. It is important that end-points are recognized as repositories of highly valued data to cyber-threats.
Further, cyber-security professionals must be constantly aware of the “…administrative and technological costs of offering a high degree of protection for all federal systems…,” (Ross, Katzke, & Toth, 2005). This is not a matter of recognizing the physical end-point alone but the value and associated costs of the virtual data stored, monitored, and protected on a continual basis. FIPS 199 assists system owners in determining whether a higher level of protection is warranted, with higher associated costs, based upon an overall FIPS 199 evaluation.
Security Tools
Security monitoring tools must identify in near-real time an active threat. Examples include anti-virus or anti-malware applications used to monitor network and end-point activities. Products like McAfee and Symantec provide enterprise capabilities that help to identify and reduce threats.
Other security tools would address in whole or part the remaining NIST Security Automation Domains. These would include, for example, tools to provide asset visibility, vulnerability detection, patch management updates, etc. But it is also critical to recognize that even the best current security tools are not necessarily capable of defending against all attacks. New malware or zero-day attacks pose continual challenges to the cybersecurity workforce.
For example, DHS’s EINSTEIN system would not have stopped the 2015 Office of Personnel Management breach. Even DHS’s latest iteration of EINSTEIN, EINSTEIN 3, an advanced network monitoring and response system designed to protect federal governments’ networks, would not have stopped that attack. “…EINSTEIN 3 would not have been able to catch a threat that [had] no known footprints, according to multiple industry experts,” (Sternstein, 2015).
Not until there are a much greater integration and availability of cross-cutting intelligence and more capable security tools, can any single security tool ever be fully effective. The need for multiple security monitoring tools that provide “defense in depth” may be a better protective strategy. However, with multiple tools monitoring the same Security Automation Domains, such an approach will certainly increase the costs of maintaining a secure agency or corporate IT environment. A determination of Return on Investment (ROI) balanced against a well-defined threat risk scoring approach is further needed at all levels of the federal and corporate IT workspace.
Security Controls
“Organizations are required to adequately mitigate the risk arising from the use of information and information systems in the execution of missions and business functions,” (NIST, 2013). This is accomplished by the selection and implementation of NIST SP 800-53, Revision 4, described security controls. They are organized into eighteen families to address sub-set security areas such as access control, physical security, incident response, etc. The use of these controls is typically tailored to the security categorization by the respective system owner relying upon FIPS 199 categorization standards. A higher security categorization requires the greater implementation of these controls.
Security Information and Event Management (SIEM) Solutions
The SIEM tool plays a pivotal role in any viable “First Generation” implementation. Based on NIST and DHS guidance, an effective SIEM appliance must provide the following functionalities:
- “Aggregate data from “across a diverse set” of security tool sources;
- Analyze the multi-source data;
- Engage in explorations of data based on changing needs
- Make quantitative use of data for security (not just reporting) purposes including the development and use of risk scores; and
- Maintain actionable awareness of the changing security situation on a real-time basis,” (Levinson, 2011).
“Effectiveness is further enhanced when the output is formatted to provide information that is specific, measurable, actionable, relevant, and timely,” (NIST, 2011). The SIEM device is the vital core of a full solution that collects, analyzes, and alerts the cyber-professional of potential and actual dangers in their environment.
There are several major SIEM solutions that can effectively meet the requirements of NIST SP 800-137. They include products, for example, IBM® Security, Splunk®, and Hewlett Packard’s® ArcSight® products.
For example, Logrhythm ® was highly rated in the 2014 SIEM evaluation. Logrhythm® provided network event monitoring and alerts of potential security compromises. The implementation of an enterprise-grade SIEM solution is necessary to meet growing cybersecurity requirements for auditing of security logs and capabilities to respond to cyber-incidents. SIEM products will continue to play a critical and evolving role in the demands for “…increased security and rapid response to events throughout the network,” (McAfee® Foundstone Professional Services®, 2013). Improvements and upgrades of SIEM tools are critical to providing a more highly responsive capability for future generations of these appliances in the marketplace.
Next month we will conclude with what is a first-generation ConMon architecture, and look to the growing developments in Data Science, Big Data and Machine Learning that will take us beyond the First-Gen concept.
Next Month’s Update: First-Generation ConMon and Beyond
Endnotes for “Continuous Monitoring: A More Detailed Discussion”
Balakrishnan, B. (2015, October 6). Insider Threat Mitigation Guidance . Retrieved from SANS Institute Infosec Reading Room: https://www.sans.org/reading-room/whitepapers/monitoring/insider-threat-mitigation-guidance-36307
Caralli, R. A. (2004, December). Managing Enterprise Security (CMU/SEI-2004-TN-046). Retrieved from Software Engineering Institute: http://www.sei.cmu.edu/reports/04tn046.pdf
Committee on National Security Systems. (2010, April 26). National Information Assurance (IA) Glossary. Retrieved from National Counterintelligence & Security Center: http://www.ncsc.gov/nittf/docs/CNSSI-4009_National_Information_Assurance.pdf
Department of Defense. (2014, March 12). DOD Instructions 8510.01: Risk Management Framework (RMF) for DoD Information Technology (IT). Retrieved from Defense Technical Information Center (DTIC): http://www.dtic.mil/whs/directives/corres/pdf/851001_2014.pdf
GSA. (2012, January 27). Continuous Monitoring Strategy & Guide, v1.1. Retrieved from General Services Administration: http://www.gsa.gov/graphics/staffoffices/Continuous_Monitoring_Strategy_Guide_072712.pdf
Joint Medical Logistics Functional Development Center. (2015). JMLFDC Continuous Monitoring Strategy Plan and Procedure. Ft Detrick, MD.
Kavanagh, K. M., Nicolett, M., & Rochford, O. (2014, June 25). Magic Quadrant for Security Information and Event Management. Retrieved from Gartner: http://www.gartner.com/technology/reprints.do?id=1-1W8AO4W&ct=140627&st=sb&mkt_tok=3RkMMJWWfF9wsRolsqrJcO%2FhmjTEU5z17u8lWa%2B0gYkz2EFye%2BLIHETpodcMTcVkNb%2FYDBceEJhqyQJxPr3FKdANz8JpRhnqAA%3D%3D
Kolenko, M. M. (2016, February 18). SPECIAL-The Human Element of Cybersecurity. Retrieved from Homeland Security Today.US: http://www.hstoday.us/briefings/industry-news/single-article/special-the-human-element-of-cybersecurity/54008efd46e93863f54db0f7352dde2c.html
Levinson, B. (2011, October). Federal Cybersecurity Best Practices Study: Information Security Continuous Monitoring. Retrieved from Center for Regulatory Effectiveness: http://www.thecre.com/fisma/wp-content/uploads/2011/10/Federal-Cybersecurity-Best-Practice.ISCM_2.pdf
McAfee® Foundstone® Professional Services. (2013). McAfee. Retrieved from White Paper: Creating and Maintaining a SOC: http://www.mcafee.com/us/resources/white-papers/foundstone/wp-creating-maintaining-soc.pdf
NIST. (2011-A, August). NIST SP 800-128: Guide for Security-Focused Configuration Management of Information Systems. Retrieved from NIST Computer Security Resource Center: http://csrc.nist.gov/publications/nistpubs/800-128/sp800-128.pdf
NIST. (2011-B, September). Special Publication 800-137: Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations. Retrieved from NIST Computer Security Resource Center: http://csrc.nist.gov/publications/nistpubs/800-137/SP800-137-Final.pdf
NIST. (2012, January). NIST Interagency Report 7756: CAESARS Framework Extension: An Enterprise Continuous Monitoring Technical Reference Model (Second Draft), . Retrieved from NIST Computer Resource Security Center: http://csrc.nist.gov/publications/drafts/nistir-7756/Draft-NISTIR-7756_second-public-draft.pdf
NIST. (2013, April). NIST SP 800-53, Rev 4: Security and Privacy Controls for Federal Information Systems . Retrieved from NIST: http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf
Ross, R., Katzke, S., & Toth, P. (2005, October 17). The New FISMA Standards and Guidelines Changing the Dynamic of Information Security for the Federal Government. Retrieved from Information Technology Promotion Agency of Japan: https://www.ipa.go.jp/files/000015362.pdf
Sann, W. (2016, January 8). The Key Missing Piece of Your Cyber Strategy? Visibility. Retrieved from Nextgov: http://www.nextgov.com/technology-news/tech-insider/2016/01/key-missing-element-your-cyber-strategy-visibility/124974/
SANS Institute. (2016, March 6). Beyond Continuous Monitoring: Threat Modeling for Real-time Response. Retrieved from SANS Institute: http://www.sans.org/reading-room/whitepapers/analyst/continuous-monitoring-threat-modeling-real-time-response-35185
Sternstein, A. (2015, January 6). OPM Hackers Skirted Cutting-Edge Intrusion Detection System, Official Says . Retrieved from Nextgov: http://www.nextgov.com/cybersecurity/2015/06/opm-hackers-skirted-cutting-edge-interior-intrusion-detection-official-says/114649/

Dr. Russo is currently the Senior Data Scientist with Cybersenetinel AI in Washington, DC. He is a former Senior Information Security Engineer within the Department of Defense’s (DOD) F-35 Joint Strike Fighter program. He has an extensive background in cybersecurity and is an expert in the Risk Management Framework (RMF) and DOD Instruction 8510, which implement RMF throughout the DOD and the federal government. He holds a Certified Information Systems Security Professional (CISSP) certification and a CISSP in information security architecture (ISSAP). He has a 2017 Chief Information Security Officer (CISO) certification from the National Defense University, Washington, DC. Dr. Russo retired from the US Army Reserves in 2012 as a Senior Intelligence Officer.








